HTTPS Proxy Scanning settings
HTTPSHypertext Transfer Protocol over Secure Socket Layer (SSL). Scanning gives GFI WebMonitor visibility into secure Internet sessions (URLs starting with https://). This feature enables you to apply policies to this type of traffic and to scan the content for threats that may be present in these sites and on downloaded files .
NOTE
This feature is not available for GFI WebMonitor installed as a plug-in for Microsoft Forefront TMGMicrosoft Forefront Threat Management Gateway. A Microsoft product that provides firewall and web proxy services. It also enables administrators to manage Internet access through policies. It is the successor of the Microsoft ISA Server and is part of the Microsoft Forefront line of business security software..
With HTTPS Proxy Scanning enabled, GFI WebMonitor can monitor and block traffic within an encrypted stream. This includes blocking and Anti-VirusUnwanted software that infects a computer. scanning of downloads within that stream. HTTPS inspection decrypts the data in the connection coming from the client, then processes the traffic, and encrypts the traffic going to the target web server.
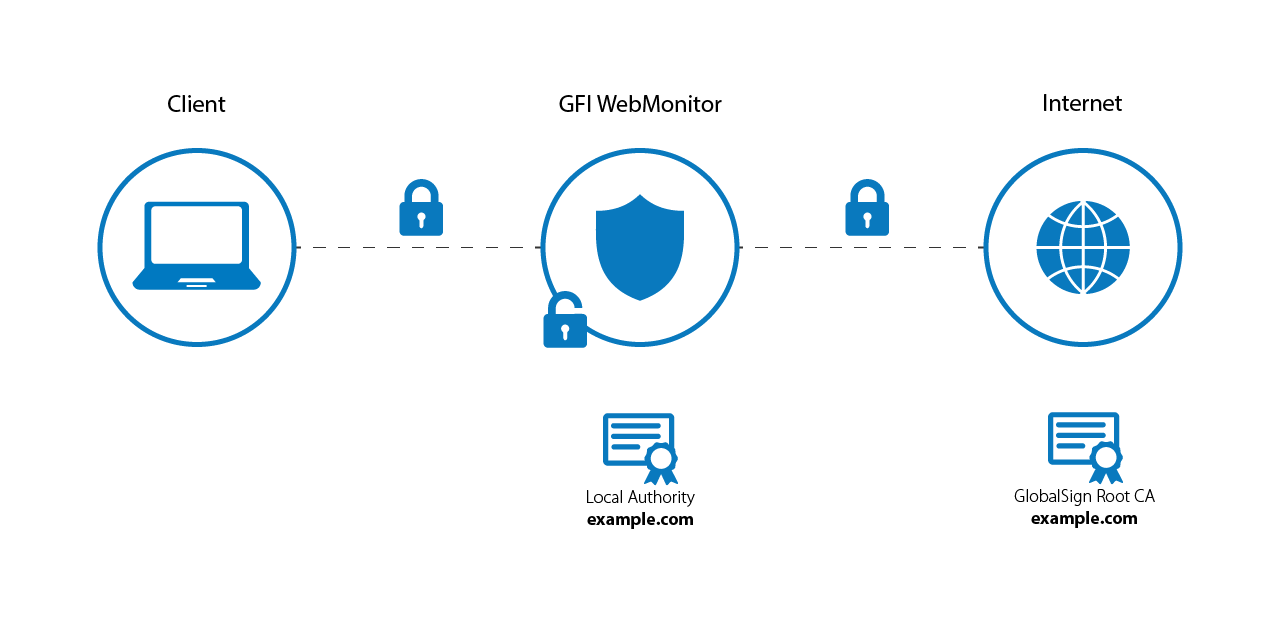
HTTPS traffic flow
The actual data that is passed between source and destination is not shown because GFI WebMonitor cannot read the encrypted contents. Only the destination web server is shown. Therefore, an administrator cannot see details of the data sent, such as account information, usernames and passwords.
NOTE
Ensure that by enabling HTTPS Scanning you are not violating any laws in your jurisdiction or any compliance regulations for your industry.
When HTTPS inspection is enabled, two secure connections are started for each HTTPS session; one between the web server and the GFI WebMonitor Proxy and one between the GFI WebMonitor Proxy and the client browser.
NOTE
When HTTPS Scanning is not enabled, GFI WebMonitor allows users to browse HTTPS websites without decrypting and inspecting their contents.
GFI WebMonitor needs a valid certificate for these two secure connections to be established. The Internet browser must verify that the certificate is signed by a trusted Certification Authority (CA). This means that for your client machines to be able to access HTTPS sites, they need to trust the certificate used by GFI WebMonitor to sign certificates.
CA certificates trusted by Windows machines are stored in the 'Trusted Root Certification Authorities' certificate store. Export the certificate from your GFI WebMonitor and deploy it on client machines manually or through Group Policy in an Active DirectoryA technology that provides a variety of network services, including LDAP-like directory services. domain environment.
The following topics will guide you through the steps required to:
- Configure HTTPS Proxy Settings
- Create a new HTTPS Scanning certificate
- Import an existing HTTPS Scanning certificate
- Export an HTTPS Scanning certificate
- Deploy an HTTPS Inspection Certificate Manually
- Deploy an HTTPS Inspection Certificate Using GPO
NOTE
It is recommended that any HTTPS website that would be inappropriate for GFI WebMonitor to decrypt and inspect is added to the HTTPS scanning exclusion list. For more information refer to Adding Items to the HTTPS Scanning Exclusion List.