Configuring Default Classification Actions
Through the configuration parameters provided in the default classification actions, you can trigger alerts and actions based only on event classification. Example: default classification parameters can be configured to trigger email alerts for all classified events (critical, high, medium and low) but archive only critical events.
Configuring default classification actions
To configure Default Classification ActionsThe activity that will be carried out as a result of events matching specific conditions. For example you can trigger actions whenever an event is classified as critical. Actions supported by GFI EventsManager include Email alerts, event archiving and execution of scripts.:
1. From Configuration tab > Options, right-click Default Classification Actions node and Edit defaults…
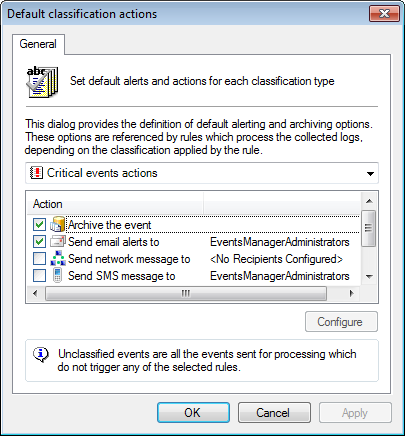
Default Classification Actions dialog
2. From the drop-down menu, select the event classification to be configured.
3. From Action list, select actions to be triggered and click Configure. The available actions are:
| Action | Description |
|---|---|
| ArchiveA collection of events stored in the SQL Server based database backed of GFI EventsManager. the event | Archives events without further processing. |
| Send email alerts to |
Click Configure and select the recipients. NOTE Ensure that users have a valid email address configured. For more information refer to Managing user accounts. |
| Send network messages to |
Click Configure and select the recipients. NOTE Ensure that users have a valid computer name/IP configured. For more information refer to Managing user accounts. |
| Send SMS message to |
Click Configure and select the recipients. NOTE Ensure that users have a valid mobile number configured. For more information refer to Managing user accounts. |
| Run file |
Click Configure and select the file to execute and specify any command-line parameters you want to pass to the file. Supported files include:
|
| Send SNMP Message | Click Configure and select the recipients. |
| Scan computer | GFI EventsManager re-audits the computer. |
| Run checks on computer |
Click Configure, select the monitoring checks you want to run when the action is triggered. Note Active Monitoring is applied to the corresponding event sources, selected from the Target computers tab. For more information refer to Creating and configuring Active Monitoring checks. Note Ensure that Monitoring Checks processing is enabled or the checks will be discarded. For more information refer to Configuring event source monitoring. |
4. Click Apply and OK.
Note
Running default actions on events classified as Low, may cause a lot of network traffic when email, SMS, network or SNMP alerts are enabled. This may also be problematic when archiving is enabled on Low importance events.