Vulnerabilities View
Display more details on the vulnerabilities found on a network and the number of affected computers. When a vulnerability is selected from the Vulnerability List, the Details section provides more information on the selected vulnerability. From the Details section click Affected computers or Unaffected computers to display a list of affected and unaffected computers.
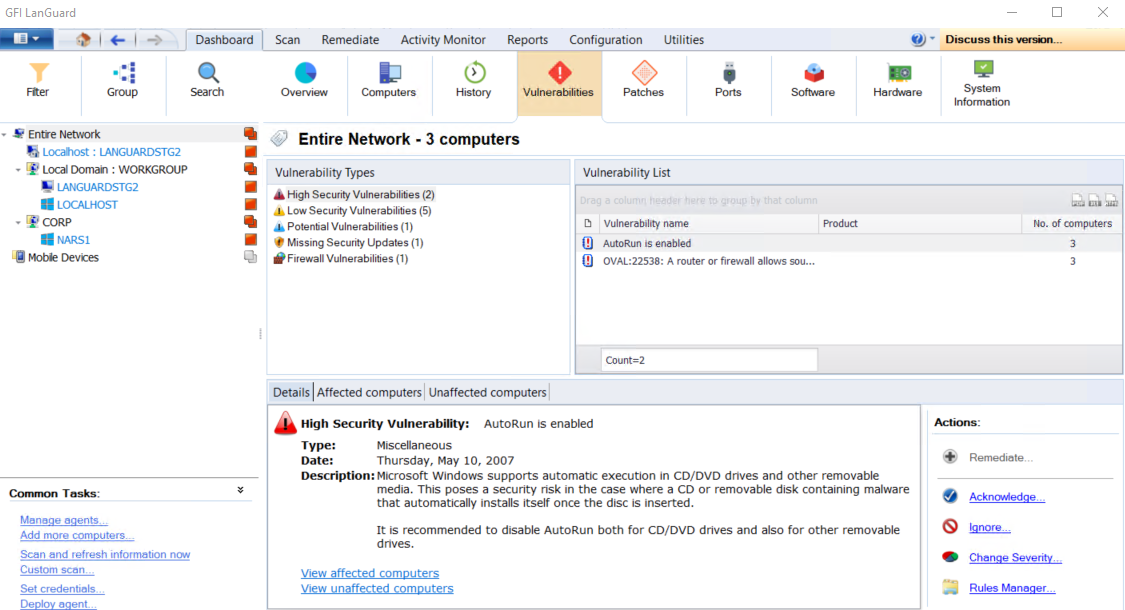
Vulnerabilities view in the DashboardA graphical representation that indicates the status of various operations that might be currently active, or that are scheduled.
NOTE
Drag and drop a column header in the designated area to group data by criteria.
Configuring actions
From the actions section select one of the actions described below to manage and remediate vulnerabilities and missing patches found in your network.