Preparing & Trusting a Certificate for Encrypted Traffic
When caching encrypted content, you need to specify a certificate that Edge Cache can use to create and sign a dynamically created certificate on behalf of the server. You need to ensure that this certificate is trusted by all the computers on your network that have traffic passing through Edge Cache. It is recommended that you create a self-signed CA certificate (as opposed to a self-signed certificate without the CA designation) to simplify the loading and trusting of the certificate by the computers in your network.
How to create a self-signed CA certificate for Edge Cache to use
When using Edge Cache for encrypted traffic, you must create and import a signing certificate in the Certificates and Keys store. This certificate and its corresponding key are used by Edge Cache to generate and sign dynamic SSL certificates for proxied sites. For all practical purposes, this certificate becomes a root certificate and you become a Root CA.
Use the following OpenSSL commands:
openssl genrsa -out myCompanyCA.key 2048
openssl req -x509 -new -key myCompanyCA.key -out myCompanyCA.cer -days 1000
-subj /CN="myCompany CA”
This will generate two files: a.key file and a .cer file that can be uploaded in the CA certificates UI.
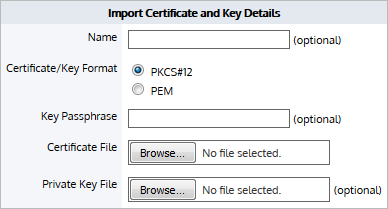
Import certificate in CA Certificates store
- Go to Configuration > System > Certificates > CA Certificates.
- Select the Import Certificate radio button.
- Optionally, Type a Name for the certificate. If no name is specified, the filename of the certificate is used. Private keys are stored separately from certificates, and are automatically named the same as the certificate, with '_key' appended to the end.
- Select the Certificate/Key Format.
- PKCS#12—Format used when the certificate and key are stored together, and usually have extensions such as
.pfxand.p12.. - PEM—Common format for certificates issued by Certificate Authorities. PEM certificates usually have extentions such as
.pem,.crt,.cer, and.key. If PEM format is selected, an additional upload field is exposed so that the private key can be uploaded with the certificate.
- If the key is password protected, in the Key Passphrase field type the password.
- In the Certificate File field, click Choose File and navigate to the file to be uploaded to the appliance.
- If the PEM format is selected, the private key must be uploaded. In the Private Key File field, click Choose File and navigate to the private key file.
- Click Import.
The certificates are displayed in the Certificates and Keys table on the CA Certificates and Keys table on the CA Certificates tab. From the tables the contents of a certificate can be viewed, or the certificate can be deleted or exported.
How to export the certificate for use on client computers
If the browsers in your network do not trust the certificate, you may get a warning or the sites may fail to load. In this case, each computer needs to import the certificate so that the certificate will be trusted when negotiating with Edge Cache over SSL.
You will need to export the certificate from the appliance and import it to the desired computers.
To export the certificate from the appliance:
- Go to Configuration > System > Certificates > CA Certificates and find your desired certificate in the list.
- Export the certificate by clicking the Export button.
- Ensure that the Export Certificate Format is set to PEM. The PEM format encodes the certificate and private key. It may include an entire certificate chain including public key, private key, and root certificates.
- Click the Save button.
How to deliver and install the certificate on machines across your network
The method used to install the trusted certificate on client machines depends upon both the browser and the operating system:
Both Chrome and Internet Explorer on Windows Machines use the Windows certificate store to trust the Exinda Edge Cache SSL certificate. Two methods are available to distribute the certificates: using a domain controller or using a manual method.
To use a Domain Controller:
In this case, it is recommended that you follow the instructions provided by Microsoft to use a domain controller to distribute the certificate:
http://technet.microsoft.com/en-us/library/cc772491.aspx
NOTE
These instructions assume that you are using a domain controller or a workstation running the domain admin MMC snapins while logged into a domain as a domain admin. Some of the elements that are referred to in the instructions will not exist if you are using Windows Server 2008 R2.
To use the manual method:
Follow this method to add the certificates to the Trusted Root Certification Authorities store on each local computer.
- In the Windows Search field, type mmc, and then press ENTER to launch the Console screen.
- Click File > Add/Remove Snap-in.
- Under Available snap-ins, click Certificates,and then click Add to move the Certificates option to the Selected snap-ins list.
- In the pop-up window, select the Computer Account option under 'This snap-in will always manage certificates for' and then click Next.
- Click Local computer, and click Finish.
- In the console tree, double-click Certificates.
- Right-click the Trusted Root Certification Authorities store.
- Click Import to import the certificates and follow the steps in the Certificate Import Wizard.
To install the trusted certificate on Linux machines for Chrome, you must use the NSS command line tools. To import a personal certificate and private key stored in a PKCS12 fiel, use the command below, substituting the details between the <> with the certificate file name.
pk12util -d sql:$HOME/.pki/nssdb -i <PKCS12_file.p12>
If the certificate was generated as a root CA certificate, use the following command, substituting the details between the <> with the certificate nickname and file name.
certutil -d sql:$HOME/.pki/nssdb -A -t "C,," -n <certificate nickname> -i <certificate filename>
Mozilla Firefox uses its own certificate store and requires a unique process to trust the certificate.
- Launch the Firefox browser.
- Go to Options > Advanced > Certificates.
- Click View Certificates.
- Click Import.
- Navigate to the certificate you generated and exported from the Exinda appliance and import it.
If installing the certificate on a MACMedia Access Control, you must use the Keychain Access program. To start the Keychain Access program,double-click certificate file.
If you are importing a CA certificate:
- Double-click the exported PEM file for the CA certificate to start the Keychain Access program.
- When prompted, type your computer's admin password.
- The Keychain Access window appears. The certificate has automatically been installed with no additional steps.
If you are importing a non-CA certificate:
- Double-click the exported PEM file for the non-CA certificate to start the Keychain Access program.
- When prompted, type your computer's admin password.
- In the Keychain Access window, select the System keychain to install for all users on the machine, or Login keychain to install only for the current user account.
- Find the desired certificate in the list and right-click and select Get Info.
- In the Trust section, select Always Trust for the When using this certificate drop-down list.