Configuring event source logon credentials
Use the Logon Credentials tab in the properties dialog to:
- View logon credentials settings
- Edit logon credentials settings.
During event processing, GFI EventsManager must remotely log-on to the target computers. This is required in order to collect log data that is currently stored on the target computers and to pass this data on to the event processing engine(s).
To collect and process logs,GFI EventsManager must have administrative privileges over the target computers. By default, GFI EventsManager will log-on to target computers using the credentials of the account under which it is currently running; however, certain network environments are configured to use different credentials to log on to workstations and servers with administrative privileges.
As an example, for security purposes, you might want to create an administrator account that has administrative privileges over workstations only and a different account that has administrative privileges over servers only.
To configure event source properties:
1. From Configuration tab > Event Sources > Group Type, select Event Sources Groups.
2. To configure settings of a:
- Computer group - right-click on the computer group to configure, and select Properties
- Single event source - right-click on the source to configure, and select Properties.
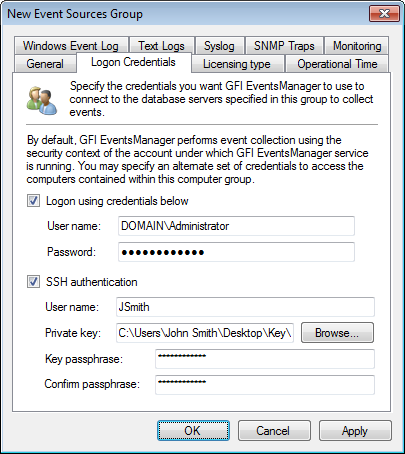
Configuring alternative logon credentials
3. Click Logon Credentials tab.
4. Select/unselect Logon using credentials below to use/stop using alternate logon credentials. Key in a username and password.
Note
Alternate logon credentials enable you to use different usernames and passwords to log into remote computers. You can set alternate credentials for a group of event sources or for each event source.
Members of an event source group can be configured to inherit credentials from the parent group.
5. Select/unselect SSH authentication to use/stop using SSH authentication.
Note
SSH uses public-key cryptography to authenticate the remote computer and allow it to authenticate the user, if necessary. This is a security protocol for Linux and Unix based computers.
6. Click Browse... to select the Private key file.
7. Key in the key passphrase and reenter it for confirmation.
8. Click Apply and OK.