Creating new events processing rules
To create a new event processing rule:
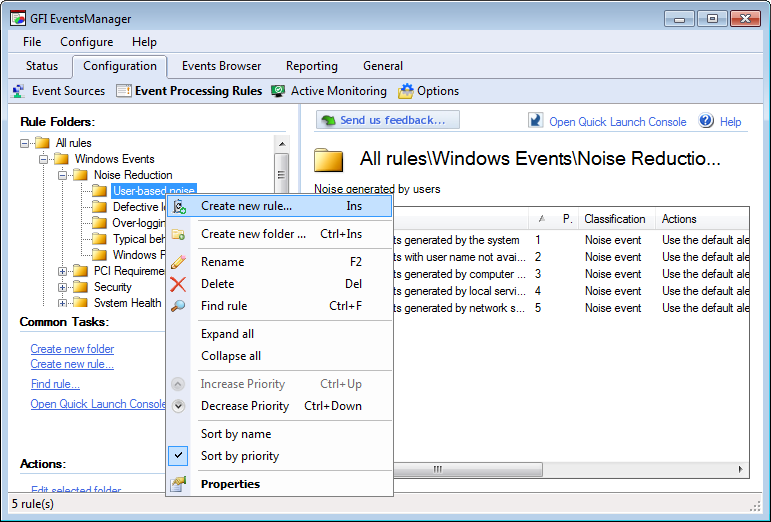
1. Click Configuration tab > Event Processing Rules.
Creating a new rule
2. Right-click the rule-set where the new rule will be created and click Create new rule…
3. Specify the name and description (optional) for the new rule. Click Next.
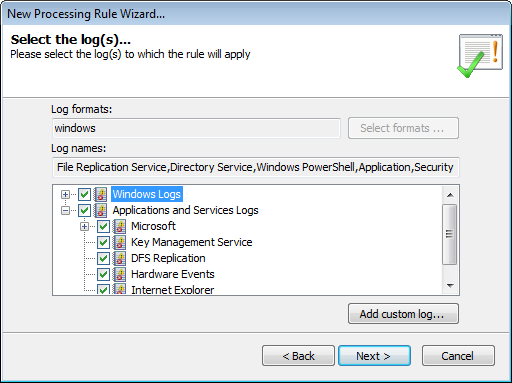
Select the logs which the rule will be applied to
4. Select the event logs to which the rule applies.
5. (Optional) Click Add custom log… to insert an event log which you pre-configured. Click Next. For more information refer to Collecting custom events.
Note
For SQL Audit, Oracle Audit, Syslogs, Text Logs and SNMP TrapsNotifications/alerts generated and transmitted by active network components (Example: hubs, routers and bridges) to SNMP server(s) whenever important events such as faults or security violations occur. Data contained in SNMP Traps may contain configuration, status as well as statistical information such as number of device failures to date. messages, specify the full path of the object’s log folder; example: “C:\W3C\logs”.
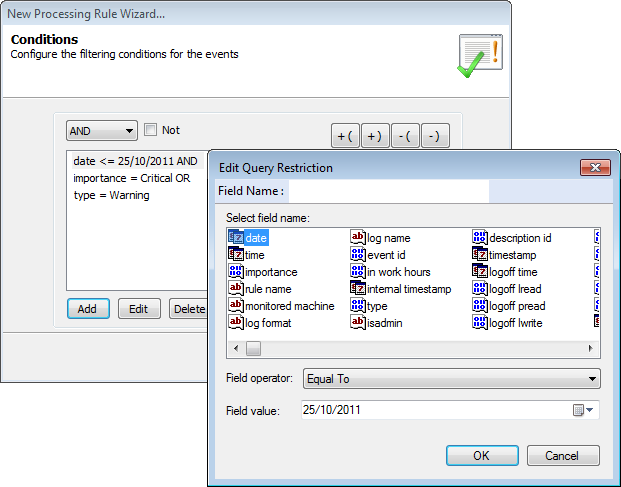
Configure the rule conditions
6. Click Add to select a field on which to base the query condition. For the selected field, specify the Field Operator and Field Value. Click OK.
Note
Repeat this step until all the required fields are selected.
Note
To filter events that refer to an administrator user (events having the security identifier SID that identifies a logon administrator session), ensure that if the event source is a domain member, the domain controller must also be added as an event source. For more information refer to Creating a new event source group.
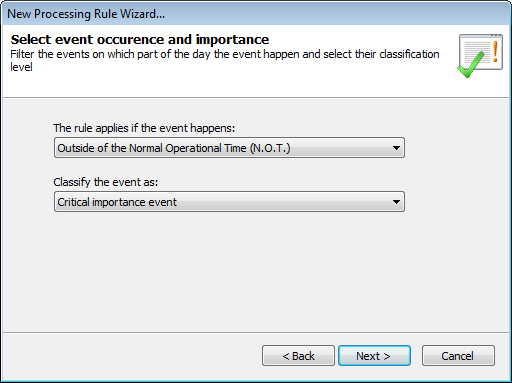
Select event occurrence and importance
7. Specify the time when the rule is applicable. Example: anytime, during working hours or outside working hours. Working and non-working hours are based on the operational time parameters configured for your event sources. For more information refer to Configuring event source operational time.
8. Select the classification (critical, high, medium, low or noise) that will be assigned to events that satisfy the conditions in this rule. Click Next.
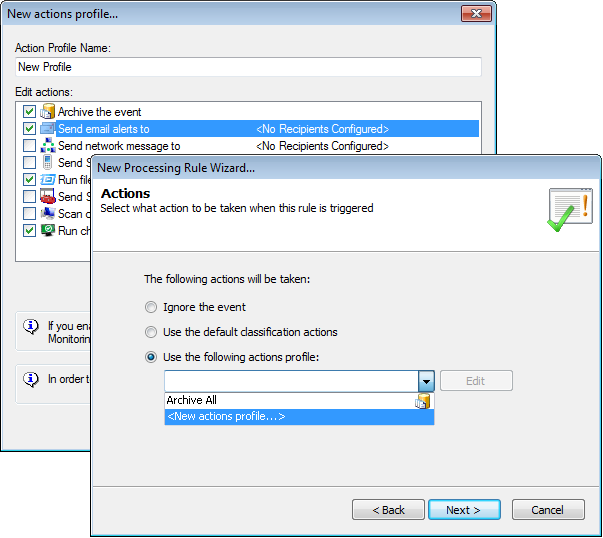
Select the triggered action
9. Specify which actions are triggered by this rule and click Next. Available actions are:
| Action | Description |
|---|---|
| Ignore the event | Select this option so that GFI EventsManager will ignore the event and not trigger any actions or notifications. |
| Use the default classification actions |
Select this option to use the pre-configured Default Classification ActionsThe activity that will be carried out as a result of events matching specific conditions. For example you can trigger actions whenever an event is classified as critical. Actions supported by GFI EventsManager include Email alerts, event archiving and execution of scripts.. |
| Use the following actions profile |
The ArchiveA collection of events stored in the SQL Server based database backed of GFI EventsManager. All profile is added by default. To create a new profile: 1. From the drop-down menu, select <New actions profile...>. This launches the New actions profile... dialog. 2. Specify a name for the new profile in the Action Profile Name text box. 3. Select the actions that you want the profile to perform. The following actions are available:
Note If Run checks on computer is selected, ensure that the computer has monitoring checks processing enabled. For more information refer to Configuring event source monitoring. 4. For each action you select, click Configure to set the parameters. |
10. Click Apply and OK.
Note
Assign the new rule(s) to your event sources. For information about how to collect event logs and process them using the specified events processing rules, refer to Collecting Event Logs.