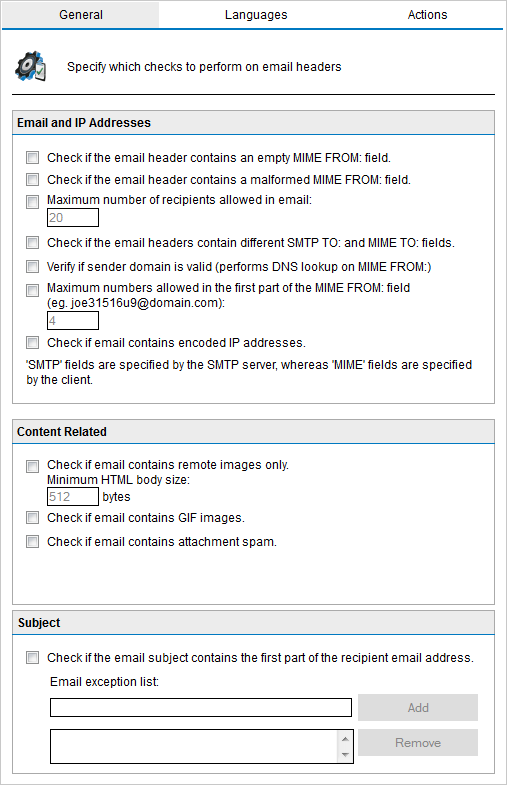
| Check if the email header contains an empty MIME FROM: field. |
Checks if the sender has identified himself in the From: field. If this field is empty, the message is marked as spam. |
| Check if the email header contains a malformed MIME FROM: field. |
Checks if the MIME from field is a correct notation as defined in the RFCs. |
| Maximum number of recipients allowed in email |
Identifies emails with large amounts of recipients and flags them as SPAM. |
| Check if the email headers contain different SMTP TO: and MIME TO: fields. |
Checks whether the SMTP to: and MIME to: fields are the same. The spammers email server always has to include an SMTP to: address. However, the MIME to: email address is often not included or is different.
NOTE: This feature identifies a lot of spam, however some list servers do not include the MIME to: either. It is therefore recommended to whitelist newsletter sender address to use this feature.
|
| Verify if sender domain is valid (performs DNS lookup on MIME FROM:) |
Performs a DNS lookup on the domain in the MIME from field and verifies the domain validity.
NOTE: Ensure that the DNS server is properly configured to avoid timeouts and slow email flow.
|
| Maximum numbers allowed in the first part of the MIME FROM: field:
|
Identifies the presence of numbers in the MIME from field. Spammers often use tools that automatically create unique reply-to: addresses by using numbers in the address. |
| Check if email contains encoded IP addresses. |
Checks the message header and body for URLs which have a hex/octal encoded IP (http://0072389472/hello.com) or which have a username/password combination (for example www.citibank.com@scammer.com).
The following examples are flagged as spam:
- http://12312
- www.microsoft.com:hello%01@123123
|
| Check if email contains remote images only.
Minimum HTML body size |
Flag emails that only have remote images and a minimal amount of text as spam. Assists in identifying ‘image only email’ spam. |
| Check if email contains GIF images. |
Checks if the email contains one or more embedded GIF images. Embedded GIF images are often used to circumvent spam filters.
IMPORTANT: Since some legitimate emails contain embedded GIF images, this option is prone to false positives.
|
| Check if email contains attachment spam. |
Checks email attachments for properties that are common to attachments sent in spam email. This helps in keeping up with the latest techniques used by spammers in using attachments to send spam. |
| Check if the email subject contains the first part of the recipient email address. |
Identifies the personalized spam email, where spammers frequently include the first part of the recipient email address in the subject.
|