Configuring Vulnerabilities
The Vulnerability Assessment Options tab enables you to configure which Microsoft®/non-Microsoft® and Security/non-Security updates are checked when scanning targets with the selected profile.
The following sections provide you with information about:
To enable vulnerability scanning:
1. Launch GFI LanGuard.
2. Click the GFI LanGuard button and select Configuration > Scanning Profile Editor. Alternatively, press CTRL + P to launch the Scanning Profiles Editor.
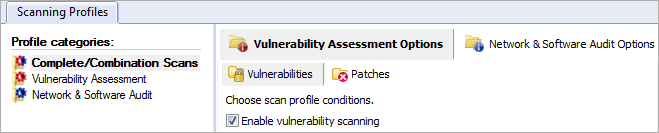
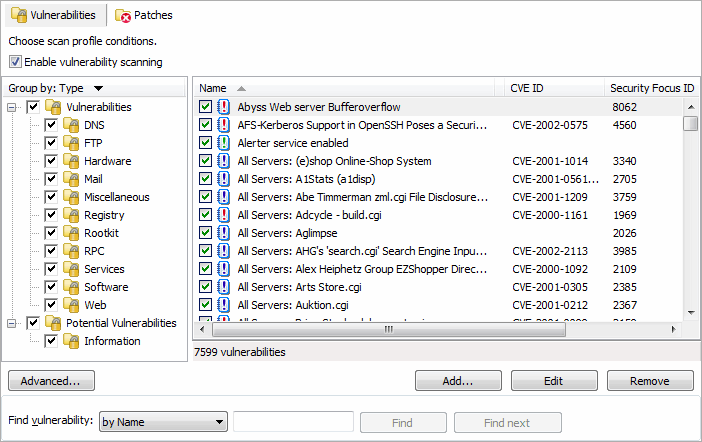
Enabling vulnerability scanning for the selected scanning profile
3. From the Vulnerability Assessment Options tab, click Vulnerabilities sub–tab.
4. Select the scanning profile to customize from the left pane under Profiles.
5. In the right pane, select Enable Vulnerability Scanning.
NOTE
Vulnerability scanning is configured on a scan profile by scan profile basis. If in a particular profile this option is not selected, no vulnerability tests will be performed in the security audits carried out by this scanning profile.
To specify which vulnerabilities will be enumerated and processed by a scanning profile during a security audit:
1. From Vulnerability Assessment Options tab, select the scanning profile to customize from the left pane under Profiles.
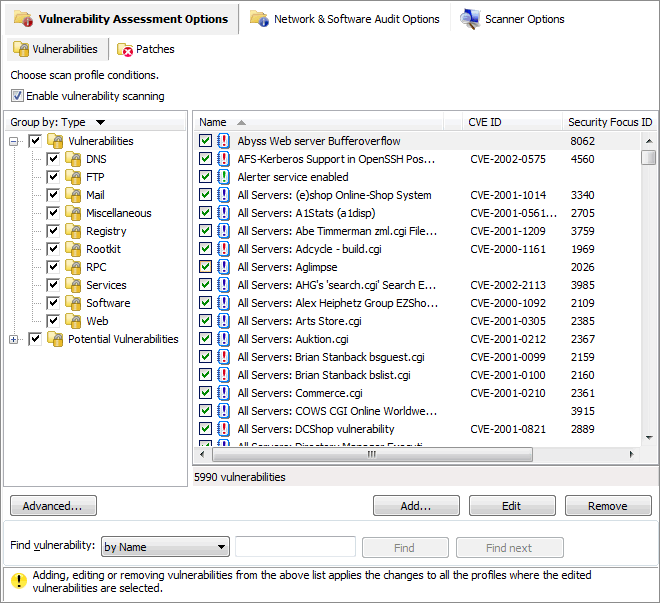
Select the vulnerability checks to be run by this scanning profile
2. In the right pane, select the vulnerability checks to execute through this scanning profile.
All the checks listed in the Vulnerabilities tab have specific properties that determine when the check is triggered and what details will be enumerated during a scan.
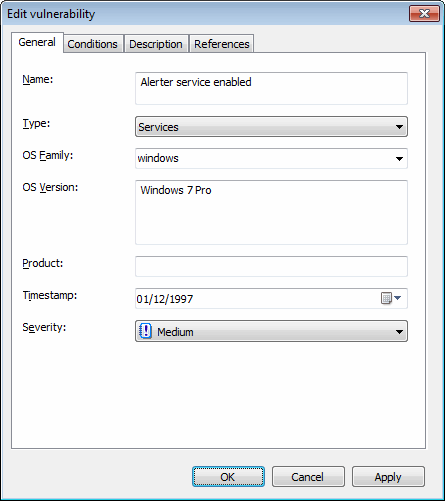
Vulnerability properties dialog: General tab
To change the properties of a vulnerability check:
1. Right–click on the vulnerability to customize, select Properties.
2. Customize the selected vulnerability check from the tabs described below:
| Tab | Description |
|---|---|
| General | Use this tab to customize the general details of a vulnerability check including vulnerability check name, vulnerability type, OS family, OS version, Product, Timestamp and Severity. |
| Conditions | Use this tab to configure the operational parameters of this vulnerability check. These parameters will define whether a vulnerability check is successful or not. |
| Description | Use this tab to customize the vulnerability check description. |
| References | Use this tab to customize references and links that lead to relevant information in the OVALA standard that promotes open and publicly available security content, and standardizes the transfer of this information across the entire spectrum of security tools and services., CVE, MS Security, Security Focus and SANSAn acronym for System Administration, Networking and Security research organization. An institute that shares solutions regarding system and security alerts. TOP 20 reports. |
3. Click on OK to save your settings.
The Conditions tab enables you to add or customize conditions, which define whether the computer or network being scanned is vulnerable, or not. It is therefore of paramount importance that any custom checks defined in this section are set–up by qualified personnel that are aware of the ramifications of their actions.
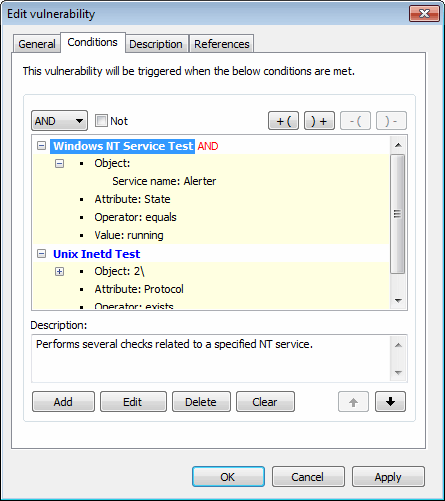
Vulnerability conditions setup tab
To add a vulnerability check condition:
1. From Vulnerability Assessment Options tab > Vulnerabilities sub-tab, right-click a vulnerability from the list of vulnerabilities and select Properties.
2. From the Edit vulnerability dialog, click Conditions tab >Add.
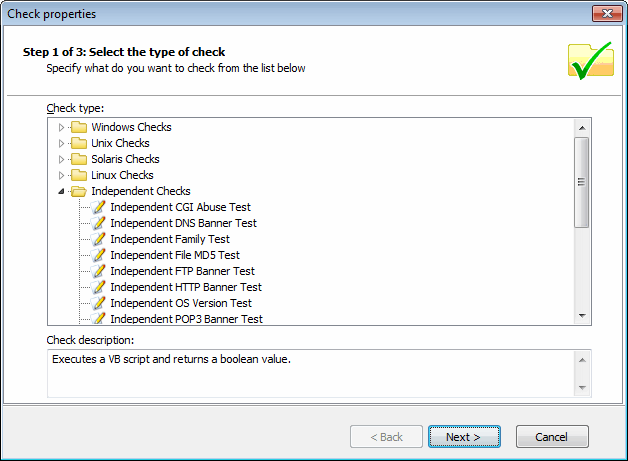
Check properties wizard - Select check type
3. Select the type of check to be configured and click Next.
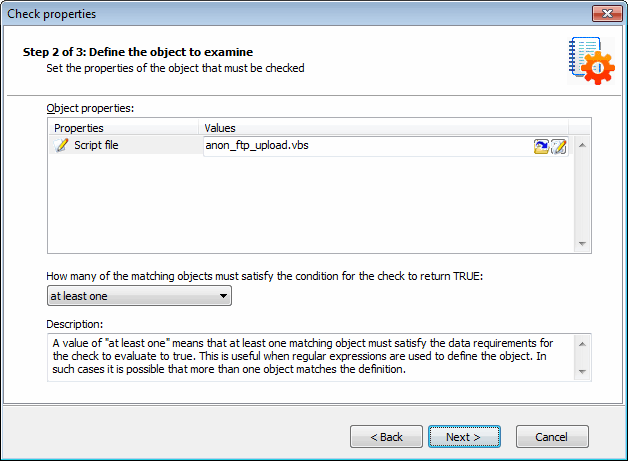
Check properties wizard - Define the object to examine
4. Define the object to examine and click Next.
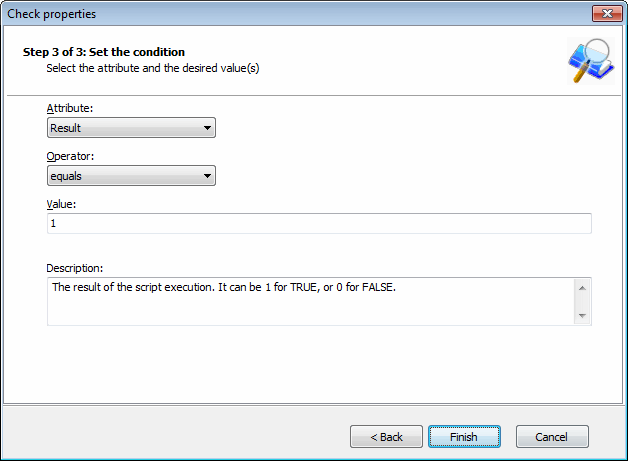
Check properties wizard - Set required conditions
5. Specify required conditions and click Finish to finalize your settings.
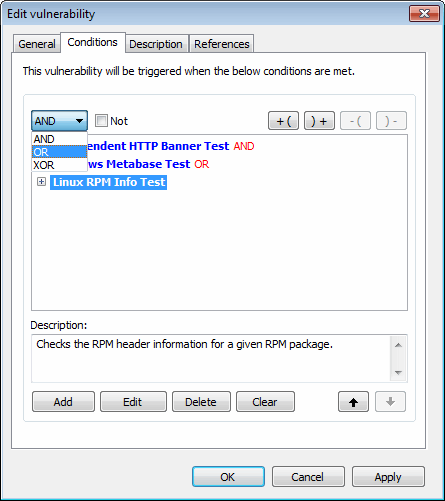
Check properties wizard - Defining conditional operators
6. If more than one condition is set up, define conditional operators and click OK to finalize your configuration settings.
Advanced vulnerability options
7. (Optional) Click Advanced in the Vulnerabilities tab to launch the advanced vulnerabilities scanning options.
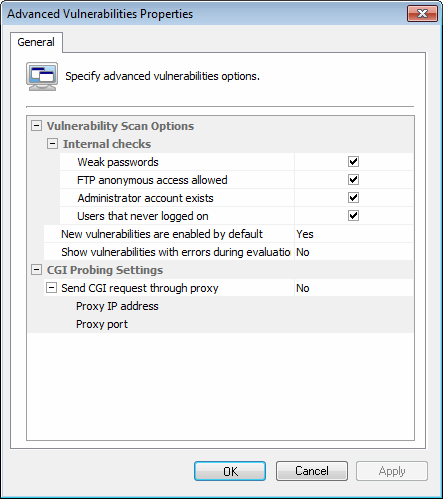
Advanced vulnerability scanning dialogs
The options in Advanced Vulnerabilities Options are used to:
- Configure extended vulnerability scanning features that check your target computers for weak passwords, anonymous FTPA protocol used to transfer files between network computers. access, and unused user accounts.
- Configure how GFI LanGuard handles newly created vulnerability checks.
- Configure GFI LanGuard to send CGI requests through a specific proxy server. This is mandatory when CGI requests will be sent from a computer that is behind a firewall to a target web server that is ‘outside’ the firewall. For example, Web servers on a DMZA section of a network that is not part of the internal network and is not directly part of the Internet. Its purpose typically is to act as a gateway between internal networks and the internet..
The firewall will generally block all the CGI requests that are directly sent by GFI LanGuard to a target computer that is in front of the firewall. To avoid this, set the Send CGI requests through proxy option to ‘Yes’ and specify the name/IP address of your proxy server and the communication port which will be used to convey the CGI request to the target.