Securing Kerio Connect
You can secure your Kerio Connect by:
- Restricting communication on firewall to necessary IP addresses and ports
- Creating a strong passwords policy
- Configuring a security policy
- Configuring an SMTP server
- Set a minimum TLS Version
- Configuring Two-Factor Authentication
- Using antispam and antivirus
- Enabling DKIM signature
- Enabling sender anti-spoofing protection
- Encrypting data
Configuring your firewall
If you install Kerio Connect in a local network behind a firewall, map these ports as follows:
| Service (default port) | Incoming connection |
|---|---|
| SMTPSimple Mail Transport Protocol - An internet standard used for email transmission across IP networks. (25) | allow |
| SMTPS (465) | allow |
| SMTP Submission (587) | allow |
| POP3Post Office Protocol 3 - A protocol used by local email clients to retrieve emails from mailboxes over a TCP/IP connection. (110) | deny |
| POP3S (995) | allow |
| IMAPInternet Message Access Protocol - One of the two most commonly used Internet standard protocols for e-mail retrieval, the other being POP3. (143) | deny |
| IMAPS (993) | allow |
| NNTPNetwork News Transfer Protocol - A transfer protocol for discussion groups over the Internet. (119) | deny |
| NNTPS (563) | allow |
| LDAPLightweight Directory Access Protocol - A protocol that enables users to access centrally managed contacts. (389) | deny |
| LDAPS (636) | allow |
| HTTPHypertext Transfer Protocol - A protocol for exchange of hypertext documents in HTML. (80, 4040, 8800) | deny |
| HTTPSSecure version of secured by SSL. (443, 4040, 8843) | allow |
Password policy
Read Password policy in Kerio Connect for detailed information on user passwords.
Configuring a secure connection to Kerio Connect
Kerio Connect can do either of the following:
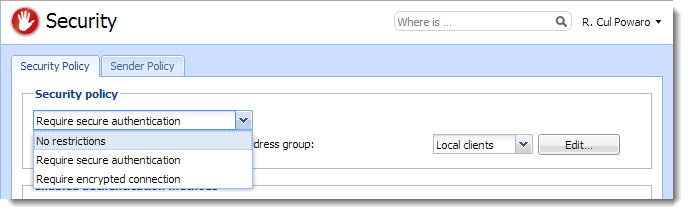
Go to Configuration > Security > Security Policy to select your preferred security policy.
You can define a group of IP addresses that can authenticate insecurely (for example, from local networks).
Securing user authentication
If you select the Require secure authentication option, users must authenticate securely when they access Kerio Connect.
You can select any of the following authentication methods:
- CRAM-MD5 — password authentication using MD5 digests
- DIGEST-MD5 — password authentication using MD5 digests
- NTLMNT LAN Manager - Security protocols that provide authentication for Windows networks. — use only with Active Directory
- SSLSecure Sockets Layer - A protocol that ensures integral and secure communication between networks. tunnel if no authentication method is used
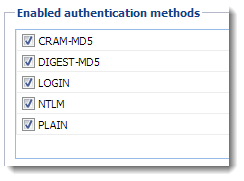
If you select more than one method, Kerio Connect performs the first available method.
NOTE
If users' passwords are saved in the SHA format:
- Select PLAIN and/or LOGIN.
- Do not map users from a directory service.
Data Encryption
NOTE
- This feature is only available for users running Kerio Connect v9.2.7 and above on Linux.
- Data Encryption is not supported on external or removable disks and, on multi-volume data storage.
- The initial encryption and decryption process takes considerable amount of time to complete based on the size of the email data. It is recommended to not interrupt the process as this will result in a corrupted email store. Email delivery is also unavailable during this time.
Enabling Encryption
You can configure Kerio Connect to encrypt user settings, logs, system configuration, and messages saved to the disk.
IMPORTANT
Encryption is bound to a specific storage device, so if you plan to change the hardware you must first disable encryption. Also, encryption results in more resources being utilized so performance maybe impacted.
- In the Kerio Connect administration interface, go to Configuration > Advanced Options > Store Directory.
- Go to the Data Encryption section.
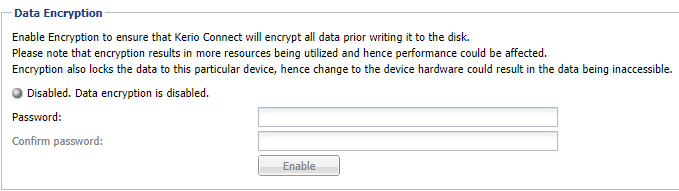
The data encryption tab
- Key-in the Password and re-enter to confirm the same.
IMPORTANT
Once encryption is enabled, the password cannot be changed. Remember this password, as you would require it to decrypt data.
- Click Encrypt and confirm the action.
Disabling Encryption
To decrypt: data and disable encryption:
- In the Kerio Connect administration interface, go to Configuration > Advanced Options > Store Directory.
- Go to the Data Encryption section.
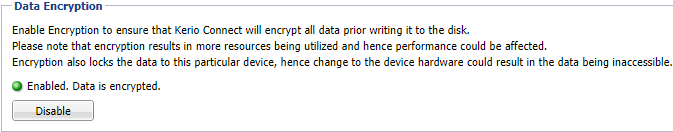
The data encryption tab
- Click Decrypt.
- Key-in the Password set while encrypting and confirm the action.
Encrypting user communication
If you select the Require encrypted connection option, clients connect to any service via an encrypted connection (the communication cannot be tapped).
You must allow the secured version of all service you use on your firewall.
NOTE
Many SMTP servers do not support SMTPS and STARTTLS. To provide advanced security, the SMTP server requires secure user authentication.