Controlling anonymous proxy traffic
Users who want to bypass security policies that prevent tools from monitoring what they are doing, typically find an open and anonymous HTTPS transparent proxy. They set their browsers to proxy all web requests through this anonymous proxy. Those requests will be encrypted with https. The security tools cannot distinguish these transactions from, say, a legitimate access to a financial website.
The Exinda Appliance can identify traffic that is served through an anonymous proxy and classify it as the Anonymous Proxy application. As such, any anonymous proxy traffic appears on the real-time monitoring screen and on other monitoring reports as"Anonymous Proxy", and can then be controlled by the Optimizer.
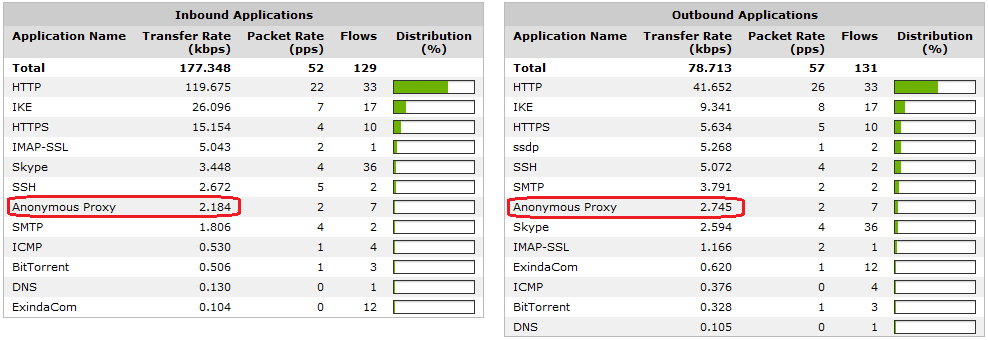
The Anonymous Proxy application is shown on the real-time monitoring screen.
The Optimizer policy configuration form below shows how to create an Optimizer policy that will block anonymous proxy traffic.
NOTE
By default, the Anonymous Proxy application is part of the Recreational application group. This means that any policy that references the Recreational application group will also be referencing the Anonymous Proxy application. If you want to block anonymous proxy traffic, the anonymous proxy discard policy must be above (earlier than) any policy that references the Recreational application group in the Optimizer policy tree.
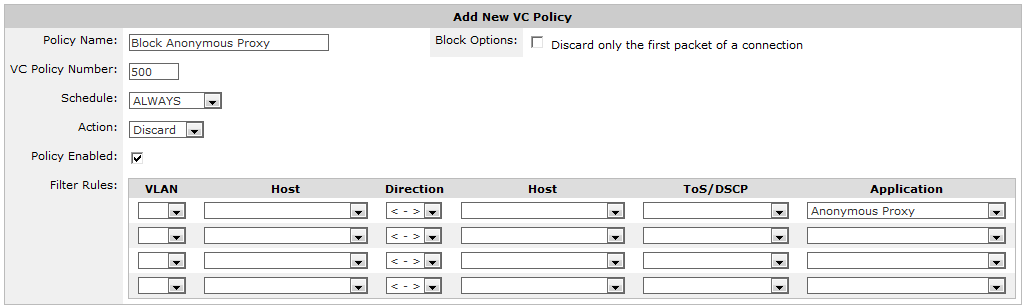
Blocking Anonymous Proxies using the Optimizer.