Application awareness in Kerio Control
NOTE
Watch the Application visibility and control video.
- Application control
- Application visibility
Application control allows Kerio Control to recognize thousands of applications in the Kerio Control network. You can then:
- Reserve or limit bandwidth for certain applications
- Allow, deny, or block traffic from or to those applications
Application visibility allows you to review used applications in Kerio Control Statistics and Active Connections.
The application awareness is available under the Kerio Control Web Filter license. For details, read Changes in licensing.
The new application awareness means that the behavior of content filtering and bandwidth management in Kerio Control changes. Rules may become more strict and can be applied to more applications or connections that they match.
To set up and use application awareness, you first enable application awareness in Kerio Control. Then you can select and use applications in the Content Filter and Bandwidth Management rules.
Enabling application awareness
Application awareness does not work in combination with Kerio Control non-transparent proxy server enabled.
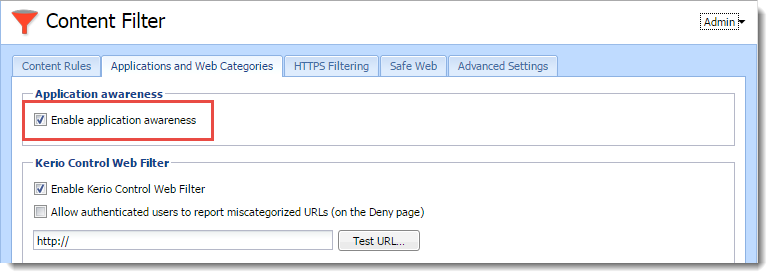
- In the administration interface, go to Content Filter.
- Click the Applications and Web Categories tab, and select Enable application awareness.
- Click Apply.
Setting content rules
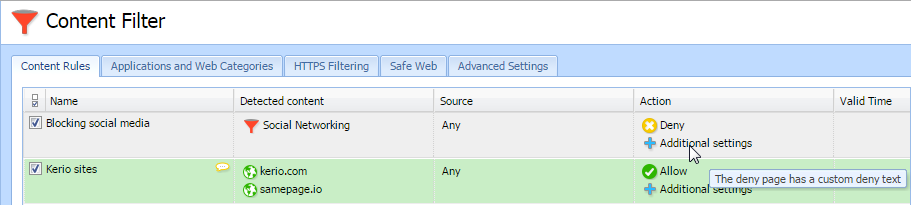
Example: Social networks
Whenever Kerio Control processes a rule that includes applications and web categories, application awareness is activated. This example shows how to set up a rule that denies all users access to social networks.
- In the administration interface, go to Content Filter.
- Click the Content Rules tab, and click Add.
- In the table, type a name for the rule.
- Double-click in the Detected content column.
- In the Content Rule - Detected Content dialog box, click Applications and Web Categories.
- In the Applications and Web Categories dialog box, select Social Networking.
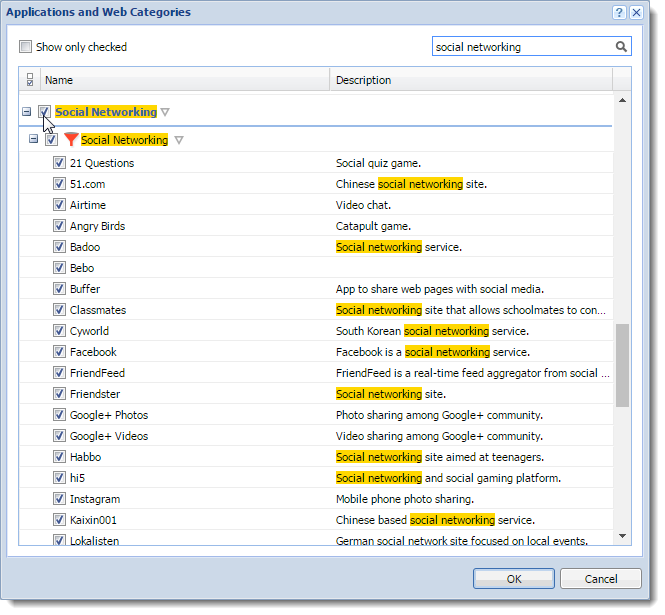
- Click OK twice.
- Do not change the Source column.
- Double-click in the Action column.
- In the Content Rule - Action dialog box, select Deny.
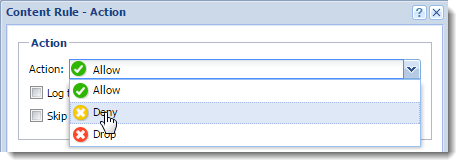
- Type a deny text that appears to users in their browsers when the rule is matched.
- Click OK.
- Click Apply.
From now on, Kerio Control refuses all attempts to use social media like Facebook or Twitter.
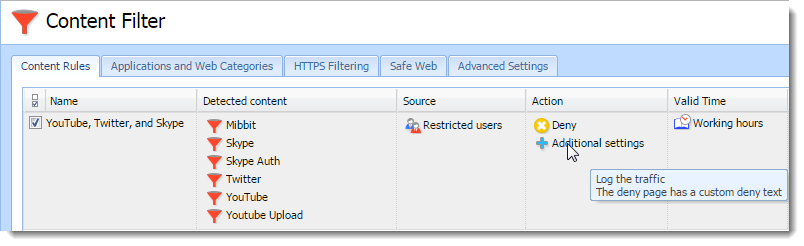
Example: YouTube, Twitter and Skype
If you don't want to be as strict as in the Example: Social networks rule, forbid access only:
- To a group of users
- To YouTube, Twitter, and Skype
- During working hours
To configure such rule:
- In the administration interface, go to Content Filter.
- Click the Content Rules tab, and click Add.
- In the table, type a name for the rule, for example, YouTube, Twitter and Skype.
- Double-click the Detected content column.
- In the Content Rule - Detected Content dialog box, click Applications and Web Categories.

- In the Applications and Web Categories dialog box, find and select all items which include YouTube, Twitter, and Skype.
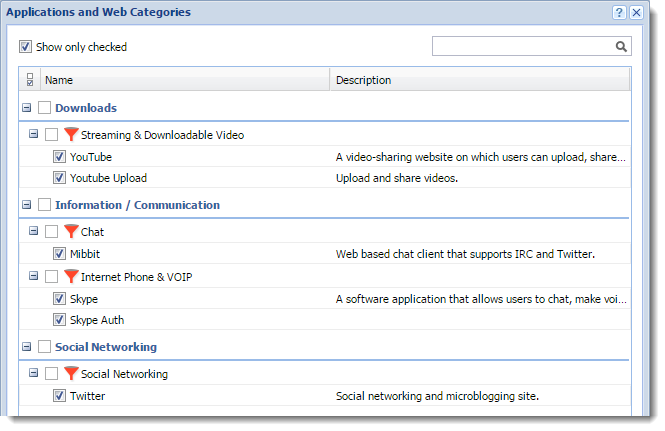
- Click OK twice.
- Double-click the Source column.
- In the Content Rule - Source dialog box, select Users and Groups.
- In the Select Items dialog box, select a group you want to restrict from using YouTube, Twitter, and Skype. For details, see Creating user groups in Kerio Control.
- Click OK twice.
- Double-click the Action column.
- In the Content Rule - Action dialog box, select Deny.

- Type a deny text that appears to users in their browsers when the rule is matched.
- Click OK.
- Double-click the Valid Time column.
- In the drop down list, select a time range. For details, see Creating time ranges in Kerio Control.
- Click Apply.
From now on, Kerio Control refuses all attempts to use YouTube, Twitter and Skype during working hours.
Setting bandwidth rules
Example: Limiting music access
Whenever Kerio Control processes a rule that includes applications and web categories, application awareness is activated. This example describes how to set up a rule limiting access to music for all users:
- In the administration interface, go to Bandwidth Management and QoSQuality of service - Network's ability to obtain maximum bandwidth and manage other network performance elements like latency, error rate and uptime..
- Click Add.
- In the table, type a name for the rule.
- Double-click in the Traffic column.
- In the Traffic dialog box, click Applications and Web Categories.
- In the Applications and Web Categories dialog box, under Entertainment / Culture, select Music.
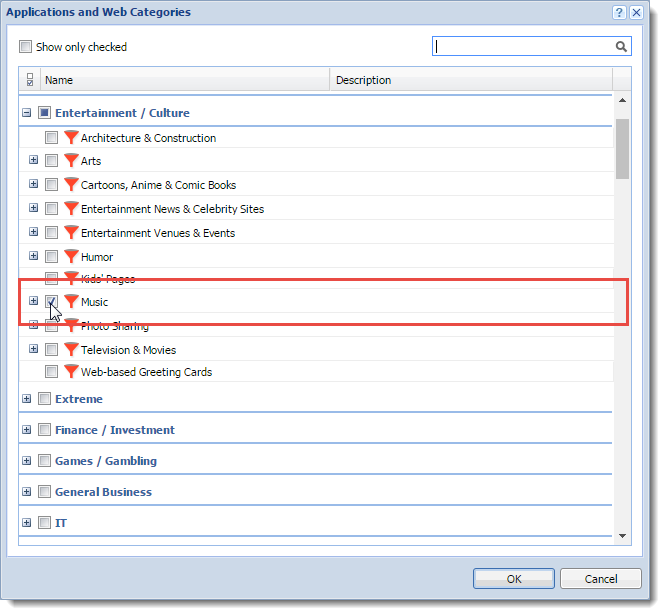
- Click OK twice.
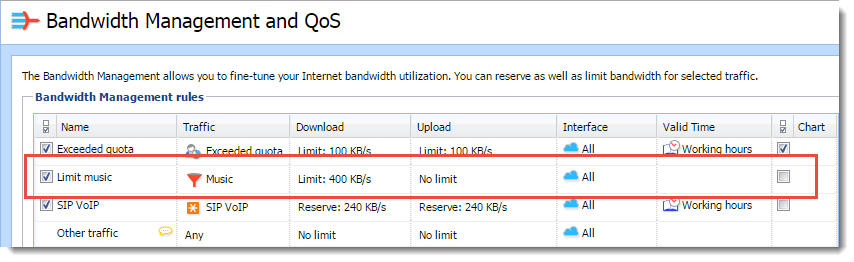
- In the Download column, limit the bandwidth. In our example, the Ethernet line is limited to 400 KB/s for music.
- Click Apply.
After applying the rule, Kerio Control limits all users who listen to music with applications like Spotify or Internet radiostations.
Application visibility in Active Connections
In the Active Connections section, you can see all applications detected on active connections:
- In the administration interface, go to Status > Active Connections.
- Right-click the column header.
- In the context menu, click Columns.
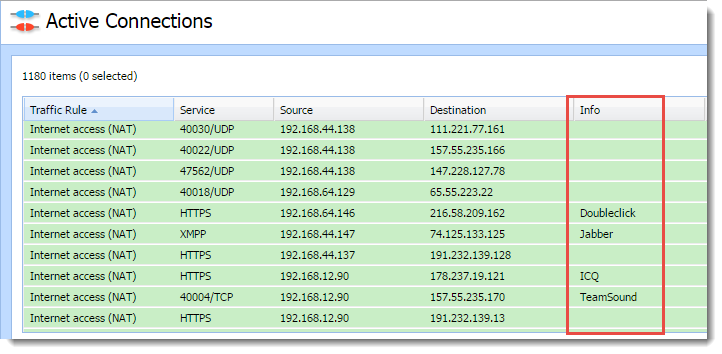
- Select Info.
From now on, the Info column displays applications detected by the application awareness.
Debugging application awareness
To run logging for the application awareness:
- In the administration interface, go to Logs > Debug.
- Right-click in the log window.
- In the context menu, select Messages.
- In the Logging Messages window, select:
- Application awareness
- Intrusion Prevention System
- General protocol inspection messages
- Click OK.
From now on, the log is running.
If you have all necessary data gathered, unselect all three log options. Logging too much information slows Kerio Control's performance.
Changes in licensing
NOTE
This section is for users upgrading from previous versions to Kerio Control 9.1.
If you have existing rules based on the following web categories, you need a Kerio Control Web Filter license.
- Peer-to-PeerA distributed application architecture that partitions tasks or workloads between peers.
- Streaming & Downloadable Audio
- Streaming & Downloadable Video
- Internet Phone & VOIP
- ICQ/AIM
- IRC
- Jabber
- MSN
- Yahoo
- IPsecInternet Protocol security - A network protocol used to encrypt and secure data sent over a network.
- Kerio VPNVirtual private network - A network that enables users connect securely to a private network over the Internet.
- L2TPLayer 2 Tunneling Protocol - A tunneling protocol used with IPsec.
- Open VPN
- PPTPPoint-to-Point Tunneling Protocol - A set of communication rules that allows to extend corporate network through private tunnels over public Internet.
- RDP
- SSHSecure Shell - A cryptographic network protocol that enables you to connect securely over an unsecured network.
- Telnet
- VNC