Eliminating Peer-to-Peer traffic
Peer-to-PeerA distributed application architecture that partitions tasks or workloads between peers. (P2PPeer-to-Peer networks are worldwide distributed systems where each node can be used both as a client and a server.) networks are worldwide distributed systems where each node can be used both as a client and a server. These networks are used for sharing of big volumes of data (this sharing is mostly illegal).
In addition to illegal data distribution, utilization of P2P networks overload lines via which users are connected to the Internet. Such users may limit connections of other users in the same network and may increase costs for the line (for example when volume of transmitted data is limited for the line).
Kerio Control provides the P2P Eliminator module which detects connections to P2P networks and applies specific restrictions. Since there is a large variety of P2P networks and parameters at individual nodes (servers, number of connections, etc.) can be changed, it is hardly possible to detect all P2P connections. However, using various methods (such as known ports, established connections, etc.), the P2P Eliminator is able to detect whether users connect to one or multiple P2P networks.
Configuring/Adding the P2P traffic rule
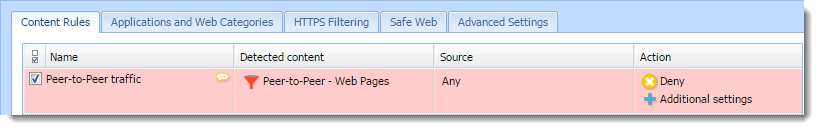
- In the administration interface, go to Content Filter.
- Select Peer-to-Peer traffic.
- Click Apply.
If your Content Filter does not include the Peer-to-Peer traffic rule, you can add one:
- Click Add.
- Type a name of the new rule (for example Peer-to-Peer traffic).
- Double-click Detected content.
- In the Content Rule - Detected Content dialog, click Add > Applications and Web Categories.
- In the Selected items dialog, select Downloads > Peer-to-Peer.
- Double-click Action.
- In the Content Rule - Action dialog, select Deny in the Action list.
- (Optional) Select Send email notification to user for non-HTTPHypertext Transfer Protocol - protocol for exchange of hypertext documents in HTML. connections. Kerio Control informs users about denying P2P traffic.
- Click Apply.
The result is displayed on figure below.
Information about P2P detection and blocked traffic can be viewed in the Status > Active Hosts section.
NOTE
If you wish to notify also another person when a P2P network is detected (e.g. the firewall administrator), define the alert on the Alerts Settings tab of the Accounting and Monitoring section.
Configuring parameters for detection of P2P networks
P2P networks are detected automatically (the P2P Eliminator module keeps running). To set the P2P Eliminator module's parameters, go to Content Filter > Advanced Settings.
It is not possible to block connections to particular P2P networks. P2P Eliminator allows to permit such services where it is guaranteed that they do not use P2P networks.
Consider the following TCPTransmission Control Protocol - ensures packet transmission./UDPUser Datagram Protocol - ensures packet transmission. port numbers as suspicious
List of ports which are exclusively used by P2P networks. These ports are usually ports for control connections — ports (port ranges) for data sharing can be set by users themselves.
Ports in the list can be defined by port numbers or by port ranges. Individual values are separated by commas while dash is used for definition of ranges.
Number of connections
Big volume of connections established from the client host is a typical feature of P2P networks (usually one connection for each file). The Number of connections value defines maximal number of client's network connections that must be reached to consider the traffic as suspicious.
The optimum value depends on circumstances (type of user's work, frequently used network applications, etc.) and it must be tested. If the value is too low, the system can be unreliable (users who do not use P2P networks might be suspected). If the value is too high, reliability of the detection is decreased (less P2P networks are detected).
Safe services
Certain legitimate services may also show characteristics of traffic in P2P networks (e.g. big number of concurrent connections). To ensure that traffic is not detected incorrectly and users of these services are not persecuted by mistake, it is possible to define list of so called secure services. These services will be excluded from detection of P2P traffic.
IMPORTANT
Default values of parameters of P2P detection were set with respect to long-term testing. As already mentioned, it is not always possible to say that a particular user really uses P2P networks or not which results only in certain level of probability. Change of detection parameters may affect its results crucially. Therefore, it is recommended to change parameters of P2P networks detection only in legitimate cases (e.g. if a new port number is detected which is used only by a P2P network and by no legitimate application or if it is found that a legitimate service is repeatedly detected as a P2P network).