Configuring adaptive response limits
Adaptive response limits allow administrators to specify rules based on combinations of data transfer amounts and/or the amount of time on the network, and then establish priorities so that different policies can be applied both before and after the limit is reached. This allows you to provide data transfer caps, throttle data transfer after a limit has been reached, or to throttle only particular types of traffic after the limit has been reached.
VERSION INFO
In 7.0.1 and above releases in the 7.0 firmware product line, the option to set Adaptive Response Limits is based on the amount of time a user is using the network.
To implement such policies, the following steps are required:
- Create a network objecta logical definition created and stored in the Exinda lilbrary, can represent any network component that defines what traffic is to be monitored.
The source network object can either be a static network object, which includes one or more subnets, or the source network object can be a dynamic network objectnetwork objects automatically updated and maintained by the Exinda appliance mapped from an Active Directory group.
- Create an adaptive response limit object. The adaptive response limit object allows administrators to specify the traffic to monitor using a network object, and what data limit or time limit should be applied and for what period. The appliance then dynamically creates a new network object that keeps track of the IPInternet protocol addresses that have exceeded their limit. When a time limit is specified, the time is tracked in increments of 5 minutes and starts counting down from the first flowthe network traffic between network objects for a given user.
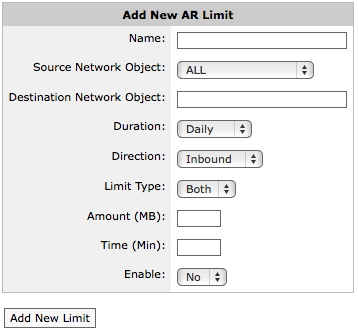
Adding a new AR limit.
- Create policies intended for the traffic matching the over-the-limit network object and policies intended for the traffic matching the source network object.
Ensure that the over-the-limit policy filters the traffic using the over-the-limit network object, and that the policy appears in the policy tree before the policies intended for the users who have not exceed their quota. Traffic attempts to match the policy tree nodes in a top-down order. Since IP addresses that have exceeded their quota will match either the destination or source network object, you need those that exceed their quota to be matched against the destination node first.
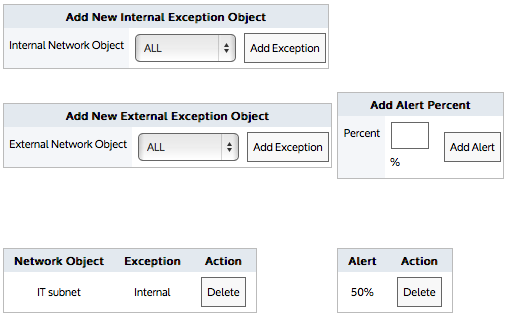
When creating the adaptive response limit object, you can create exceptions such that certain IP addresses, specified by one or more network objects, can be excluded from the limit rules. By editing the adaptive response limit object, you can specify which IP addresses are exempt from the rule. The exception network object can be internal or external. By creating an exception for an internal network object, those IP addresses will not have the limit applied to them. By creating an exception for an external network object, those IP addresses in the source network object will be excluded when they are conversing with an IP in the external exception network object.
You can also create an alert that sends an email to the Exinda Appliance email recipients when a specified quota threshold has been exceeded. The email will contain all the IP addresses that have exceeded the threshold. Note that the Info Emails checkbox must be checked for each recipient on the email configuration page.
To see examples, read Quota Enforcement in the Common Use Cases section.
Go to Configuration > Objects > Adaptive Response.
- Enter a name for the Adaptive Response Limit object.
- From the Source Network Object drop-down list, select the desired network object. The source network object can be a static network object specified as subnets, or it can be a dynamic network object based on Active Directory users or user groups.
- In the Destination Network Object field, type a name for the network object that will be dynamically created to store the IP addresses of the users that exceeded the limit.
- From the Duration drop-down list, select the time period that the limit applies to. For example, if you want to apply a 10MB cap per day, select daily. The options are daily, weekly, monthly.
- From the Direction drop-down list, select which traffic direction is counted towards the limit. The options are inbound, outbound, both.
- From the Limit Type drop-down list, select whether you want the limit to be based on data volume, the amount of time on the network, or both (meaning whichever occurs first).
- In the Amount field, specify the data volume limit, beyond which the IPs will be added to the destination network object. Specified in MB.
- In the Time field, specify the time on the network limit, beyond which the IPs will be added to the destination network object. Specified in minutes.
- If you are ready to make this adaptive response limit rule active, select Yes from the Enable drop-down list.
- Click the Add New Limit button. The object is added to the list of configured adaptive response limit objects.
As an example, consider an educational institution that has a group of students who have IP addresses in the subnet 192.168.0.0/16. Each student is allowed 10GB data transfer (uploads and downloads) per month. The resident assistants are excepted from the rule as well as students who are trying to access a particular university server.
- Edit an existing adaptive response limit object.
- In the Add Alert Percent field, type the percentage of threshold that should trigger an email. The percentage can exceed 100.
- Click the appropriate Add Alert button.
NOTE
Valid SMTPSimple Mail Transfer Protocol and email settings are required for email alerts.
The Info Emails checkbox needs to be checked for each email recipient on the Configuration > System > Network > Email tab.
- Edit an existing adaptive response limit object.
- In the Add New Internal Exception Object or Add New External Exception Object section, select the network object that specifies the IPs that you would like excluded from the adaptive response limit rule. Selecting an internal network object will exclude the associated IP addresses from the limit rule. Selecting an external network object will exclude the hosts having conversations with particular external hosts from the limit rule. For example, consider an educational institution that has a group of students who have IP addresses in the subnet 192.168.0.0/16. Each student is allowed 10GB data transfer (uploads and downloads) per month. The resident assistants are excepted from the rule as well as students who are trying to access a particular university server.
- Click the appropriate Add Exception button. Upon reaching the threshold, an email is sent that has content similar to:

Consider an educational institution that has a group of students who have IP addresses in the subnet 192.168.0.0/16. Each student is allowed 10GB data transfer (uploads and downloads) per month.
Go to Configuration > Objects > Network > Dynamic and select the appropriate dynamic network object.
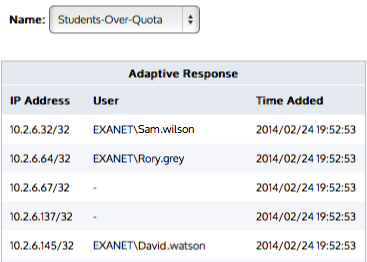
The Duration setting indicates the frequency at which the quota is reset.
- Daily Duration resets at midnight
- Weekly Duration resets at midnight Saturday night/Sunday morning
- Monthly Duration resets at the 1st of the month.
If the quota is not reached for a given day, then the quota is reset. For example, consider Daily Duration, where the quota is reset at midnight. If the time limit was set to 90 minutes and the user started using the network at 11:30pm, then the system would allow 2 hours of continuous use, which includes 30 minutes until midnight, then another 90 minutes when the new day started at midnight.