Configure SSL Acceleration Servers
SSL Acceleration provides acceleration of SSL encrypted TCPTransmission Control Protocol sessions by intercepting SSL connections to configured servers by decrypting these sessions, performing acceleration techniques, and then re-encrypting them. Only traffic to the configured servers is SSL accelerated. Any SSL traffic that the Exinda appliance sees that does not belong to a configured server is ignored.
By configuring the SSL Acceleration Server, you are specifying:
- The location of the server (IPv4 address and port)
- The SNI (Server Name Indication) which is the hostname of a virtual host when multiple secure websites are hosted on a single host where you want each website to use its own certificate
- Which certificate is used to re-encrypt the traffic
- Which certificate is used to authenticate the traffic and what type of validation to perform using that certificate
- If any CA validation is chosen, then you can choose whether to check if that CA certificate is still valid or whether it has been revoked.
NOTE
If the revocation check cannot be done or the certificate has been revoked, then the SSL Acceleration Server is disabled. If the OCSP Responder is offline, the server is disabled. The appliance periodically tests the connection and re-enables the server when it is back up. If the OCSP response verification fails or if the certificate has been revoked, then the connection is reset and the server is disabled.
NOTE
If there are any problems with the certificate or key associated with a configured SSL server (e.g., a missing key, or an expired certificate), then SSL Acceleration ignores that traffic until the issue is resolved. The traffic may still be accelerated, just not SSL-accelerated.
NOTE
The SSL Acceleration service uses port 8018 to communicate between Exinda Appliances. Please ensure this port is open for proper functionality
IMPORTANT
Before a server with an SNI extension can be added to the Exinda Appliance, the server must be added to the appliance without the SNI extension. A server without an SNI extension can be used as a fallback in event that the client is unable to process the SSL certificate with SNI. A server with the same IPInternet protocol address and port number can be added to the appliance by specifying a unique SNI extension for each server.
IMPORTANT
A server cannot be deleted if another server with the same IP address and port number, and an SNI extension has been configured on the Exinda Appliance. Servers with SNI extensions must be deleted before the server can be deleted.
Go to Configuration > System > Optimization > SSL.
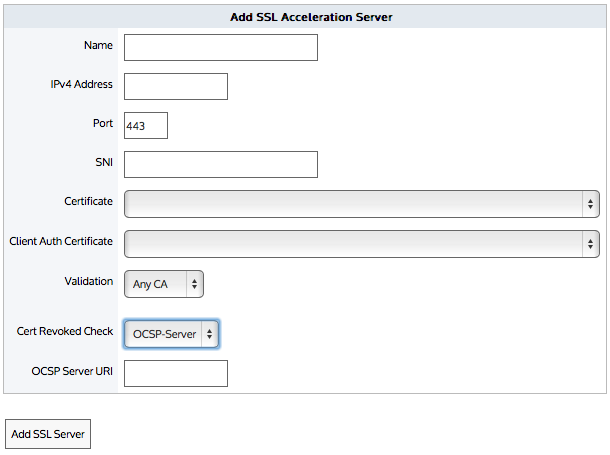
- In the Add SSL Acceleration Server area, type a name for the server or application you wish to enable for SSL Acceleration.
- Type the IPv4 Address of the server running the SSL enabled application.
- Type the Port number running the SSL enabled application on the server.
- If the server has multiple SSL certificates with a Server Name Indication (SNI) specified, type the SNI extension in the field. The server (without an SNI) must be added before the server with the same IP and port number and an SNI can be added.
- Select the Certificate to use for re-encryption of the SSL session. The certificates available here are those that are configured in the Certificate and Key page.
- Select the Client Auth Certificate to authenticate sessions on the SSL server.
- Select the type of validation to apply to the server's certificate.
- None— SSL Acceleration accepts and processes the connection even if the server's SSL certificate is invalid or expired.
- Reject— SSL Acceleration does not processes the connection under any circumstances. The connection is still accelerated, but is not SSL accelerated.
- Certificate— SSL Acceleration accepts and processes the connection only if the server's certificate matches the specific certificate named in the Client Auth Certificate field. Otherwise, the connection is not processed.
- Any CA— SSL Acceleration accepts and processes the connection if the server's certificate matches any CA certificate that is loaded on to the Exinda appliance.
- Any— SSL Acceleration accepts and processes the connection if the server's certificate matches any certificate (CA or non-CA) that is loaded on to the Exinda appliance.
- If Certificate is selected as the Validation type, select the certificate to validate against.
- If Any CA or Any is selected as the Validation type, select the Cert Revoked Check type.
- None— No check is performed. The client auth certificate is used regardless of whether the certificate is revoked or not.
- OCSP-AIA— The Online Certificate Status Protocol (OCSP) Authority Information Access (AIA) check is performed. The method uses the location of the authority embedded in the certificate to check for the certificate's revocation status. Note that if the AIA location is not specified in the certificate when this option is chosen, then the certification revoke check will not happen.
- OCSP-Server— The Online Certificate Status Protocol (OCSP) check is performed. This method presents an OCSP Server URI field where you can type the location of the authority to check for the certificate's revocation status.
- Click Add SSL Server.
The servers are displayed at the top of the page, where they can be edited or deleted.
- Locate the server in the SSL Acceleration Servers list, and click Edit.
- Modify the settings for the server, and click Apply Changes. The settings for the server are changed.
- Locate the server in the SSL Acceleration Servers list, and click Delete. Servers with SNI extensions must be deleted before the server with the same IP and port number (but without an SNI) can be deleted.
- In the confirmation dialog, click OK. The server is deleted.
If the server is disabled, check the status message in the SSL Acceleration Servers list or Remote SSL Acceleration Servers list. The list will provide feedback on why the server is disabled. Perhaps the certificate validation failed or the OCSP validation failed.
To fix the problem, you can try relaxing the certificate validation a step at a time. For example, turn off OCSP validation and see what happens. Then turn off or broaden the certification validation, such as using ANY, or ANY-CA and see what happens. You can also use the openssl client to check the SSL handshake:
openssl s_client -state -msg -connection <ip:port> -ssl3 -showcerts
openssl s_client -connect <ip:host> -tls1 -showcerts -servername <server-name>