Overview of Kerio Control
Kerio Control is a unified threat management firewall that features intrusion prevention, content filtering, activity reporting, bandwidth management, and virtual private networking. This guide provides general step-by-step instructions for deploying Kerio Control in a common scenario.
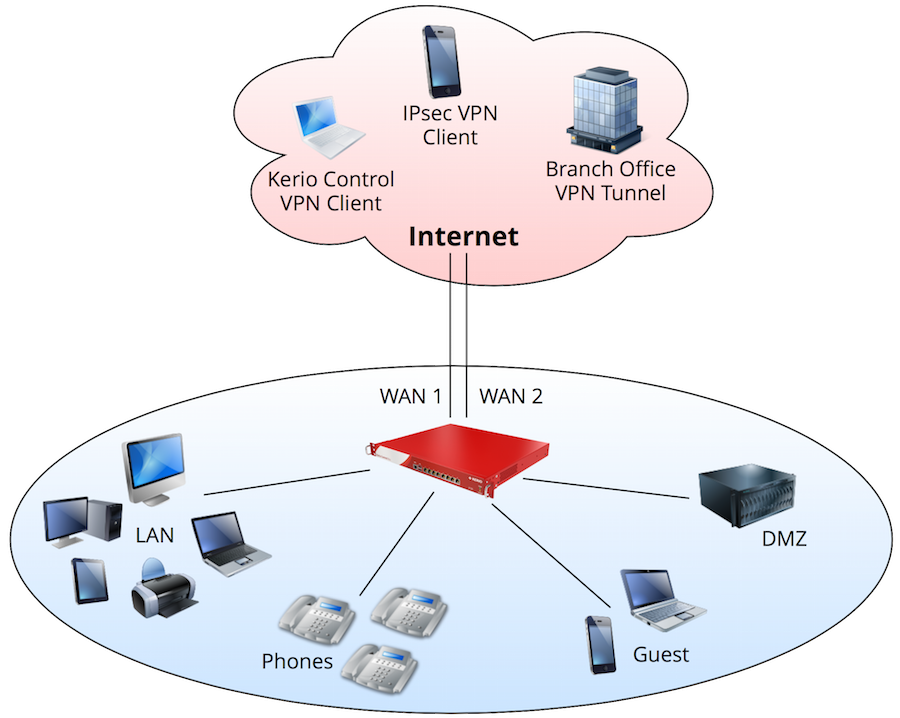
In this example:
- Kerio Control load balances between two Internet links.
- WANWide area network - A network that connects computers and other devices in a large area. 1 has five static IP addresses and hosts services for servers behind the firewall.
- WAN 2 has a dynamic IP addressAn identifier assigned to devices connected to a TCP/IP network. and primarily handles web browsing and Internet access.
- There are four separate networks behind the firewall (LANLocal area network - A network that connects computers and other devices in a small area., Phones, DMZDemilitarized zone - A security method that separates internal LAN networks from external networks., Guest).
- The DHCPDynamic Host Configuration Protocol - A protocol that automatically gives IP addresses and additional configuration to hosts in a network. server in Kerio Control automatically assigns IP configuration to all networks.
- Users authenticate against a local domain controller.
- Users authenticate via RADIUSRemote Authentication Dial-In User Service - A protocol that offers authentication, authorization, and accounting of users in a network. for web access
- Kerio Control forbids peer-to-peer networking.
- Kerio Control maintains a VPN tunnelKerio Control includes a VPN tunnel which allows to distributed offices to interconnect their offices securely. with a remote office.
- Users connect remotely using VPNVirtual private network - A network that enables users connect securely to a private network over the Internet. from computers and mobile devices.
- Kerio Control reserves 1 Mbps for VoIPVoice over Internet protocol - A digital telephone system that uses the internet as the transmission medium, rather than the PSTN. traffic.
- Kerio Control restricts guest access to a maximum of 1 Mbps.
- The company president receives a weekly report of all user activity.
- Kerio Control automatically saves its configuration to MyKerio every day.
Selecting a deployment type
Kerio Control is available as a Software, Virtual, or Hardware appliance (Hardware editions are available in North America, Australia, and the EU). The product features and functionality are nearly identical across all versions.
| Appliance | Description |
|---|---|
| Software ApplianceA special operating system designed to run on a computer. |
Downloadable ISO file Imaged onto installation media (e.g. USB drive, CD media) Installed onto standard hardware |
| Virtual AppliancePre-configured Kerio Control virtual machine image for VMware or Hyper-V. |
Available as a Virtual Hard Disk (VHD) for Microsoft Hyper-V Available in Open Virtualization Format (OVF) for VMware ESX/ESXi Available as pre-built VMware virtual guest (VMX) |
| Hardware Appliance NG100 |
3x Gb ports 1.3 GHz Dual Core Intel Bay Trail, 4 GB RAM, 32 GB SSD |
| Hardware Appliance NG110 |
3xGb Ports 2.24GHz Dual Core Intel Braswell, 8GB RAM, 32GB SSD |
| Hardware Appliance NG300 |
4x Gb ports 2.4 GHz quad core Intel Atom, 4 GB RAM, 32 GB SSD |
| Hardware Appliance NG310 |
6xGbE RJ45, 2xGbE SFP 2.2 GHz quad core Intel Atom Quad Core, 8GB, 32GB SSD |
| Hardware Appliance NG500 |
6x Gb ports 3.6 GHz quad core Intel Core i5, 4 GB RAM, 32 GB SSD |
| Hardware Appliance NG510 |
6x GbE 3.4 GHz quad core Intel Core i5, 16GB RAM, 32GB SSD |
| Hardware Appliance NG511 |
6x + 8x GbE 3.4 GHz quad core Intel Core i5, 16GB RAM, 32GB SSD |
Installing and upgrading Kerio Control
You can download the Kerio Control image from the Kerio website. For instructions on Kerio Control installation, see Installing Kerio Control. If you are installing the Virtual or Software Appliance editions, make sure your hardware meets the system requirements.
After installation, the software automatically checks for updates. The web administration notifies you when an update is ready. For more information refer to Upgrading Kerio Control.
Accessing Kerio Control
After installation, Kerio Control automatically detects your Internet and local interfaces. For successful detection of the network interfaces, connect Kerio Control to the appropriate networking equipment (e.g., modem, switch, access point and so on) prior to installation.
You can access the full administration from a web browser by inputting the IP address of the firewall. Note that your management computer must be in the same IP subnet as the firewall.
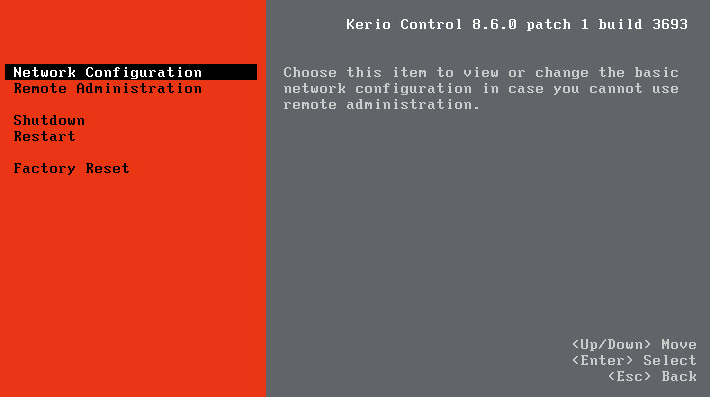
The Virtual and Software Appliance editions include a separate administration interface that the administrator can access directly from the operating system. This dialog box includes only essential features and is primarily useful when you are not able to access the web administration. Capabilities of this interface include:
- Allow remote administration from untrusted networks
- Perform a factory reset
- Shutdown/restart
- Configure TCP/IPTransmission Control Protocol/Internet Protocol - Communication protocols that connect computer hosts to the Internet. parameters
Activating Kerio Control
When the administrator first logs in to the web administration interface, the Activation Wizard opens. The wizard sets the basic system parameters:
- Select the default language
- Confirm Internet Connectivity
- Set the local date and time
- Activate the license
- Assign a password for administration
- Set alerts and notifications
- Enable management from MyKerio
See Configuring the Activation Wizard and Managing Kerio Control appliances in MyKerio for details.
Defining network interfaces and connectivity
Network interfaces in Kerio Control provide routing between local networks and the Internet. You must configure networking parameters and define your Internet connectivity before any other types of firewall configuration. The administrator can manage network interfaces and Internet connectivity in Configuration > Interfaces. Capabilities include:
- Organize interfaces into groups
- Configure Internet link load balancing
- Add VLAN interfaces
- Create VPN tunnels
- Assign TCPTransmission Control Protocol - ensures packet transmission./IP parameters to network interfaces
- Add interfaces for L2TPLayer 2 Tunneling Protocol - A tunneling protocol used with IPsec., PPPoEA type of tunneled link, which is established over top of a physical network interface., or Dial-up connections
For more information refer to Configuring network interfaces.
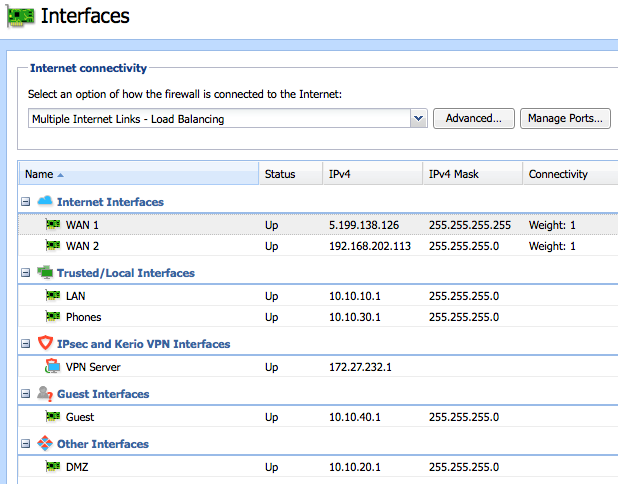
In the example scenario, Kerio Control load balances between two Internet links and routes to four local networks.
- The administrator labels each network interface.
- The administrator defines networking parameters to each network interface.
- The administrator defines additional IP addresses to WAN 1 (set in Define additional IP addresses… in the interface properties).
- The administrator moves the WAN 1 and WAN 2 interfaces into the Internet Interfaces group.
- The administrator moves the DMZ interface into the Other Interfaces group.
- The administrator moves the Guest interface into the Guest Interfaces group.For more information refer to Configuring the guest network.
- The administrator moves the LAN and Phones interfaces into the Trusted/Local Interfaces group.
- The administrator selects Multiple Internet Links - Load Balancing as the Internet connectivity.
- The administrator defines an equal link weight of 1 for each Internet interface.
Assigning parameters to local networks
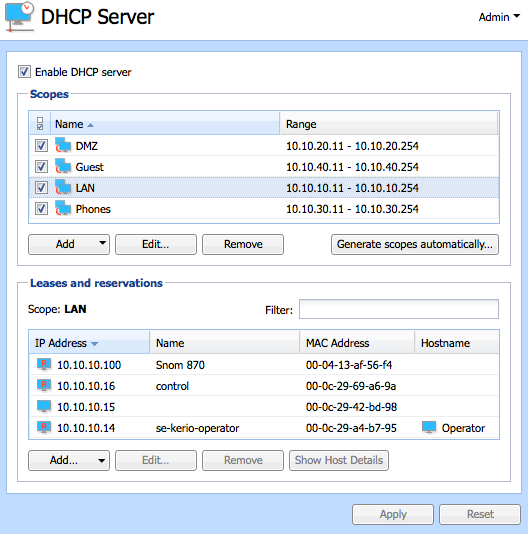
Kerio Control can simplify managing the network by acting as a Dynamic Host Configuration Protocol (DHCP) server. DHCP automatically assigns networking parameters to connected devices. The administrator can manage the DHCP server in Configuration > DHCP Server. For more information refer to DHCP server in Kerio Control.
In the example scenario, the DHCP server in Kerio Control automatically assigns IP configuration to all networks.
- The administrator enables the Kerio Control DHCP server.
- The administrator allows the firewall to generate scopes automatically.
- Devices connect to the network and receive networking parameters automatically.
- The administrator creates reservations for devices that need a permanent IP address.
Connecting to a directory service
Kerio Control can simplify user administration by authenticating users from Apple Open DirectoryA directory service for Apple based networks. or Microsoft Active DirectoryA directory service for Windows domain networks.. The administrator can manage directory services in Configuration > Domains and User Login. For more information refer to Connecting Kerio Control to directory service.
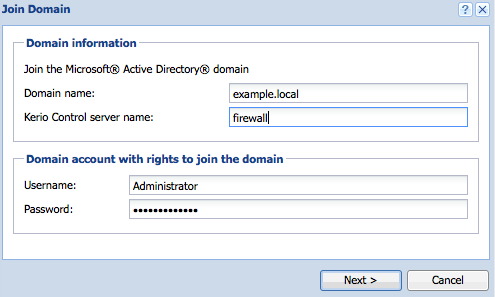
In the example scenario, users authenticate against a local domain controller.
- The administrator joins Kerio Control to the local domain.
- The administrator configures Kerio Connect to map users from the directory server.
Enforcing security and access policies
Kerio Control enforces security through Intrusion Prevention, Traffic Rules, and Kerio AntivirusAn integrated antivirus engine powered by Bitdefender.. These features configure automatically, and ensure that the firewall permits only legitimate network communication.
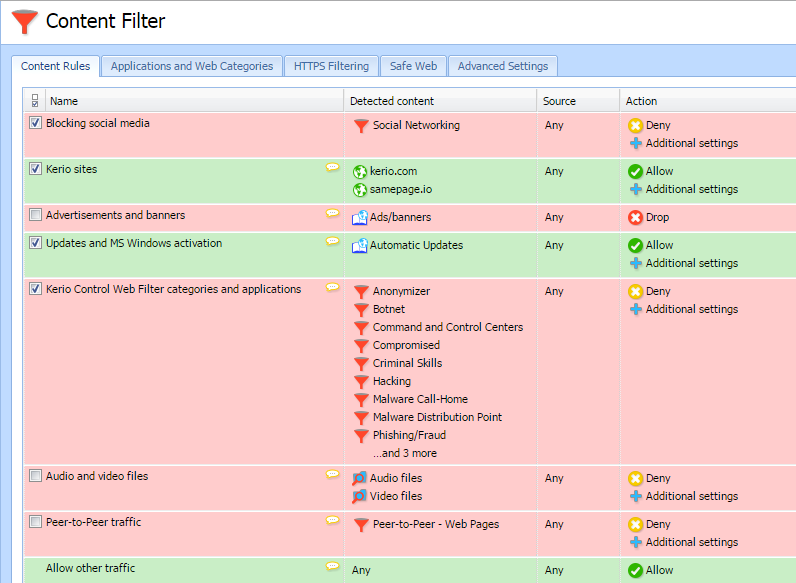
For additional security, the administrator can configure Traffic Rules and Content Rules. Content Rules define the types of permitted or denied web activities of users on the network. Examples include:
- Transfer of specific file types
- Streaming media
- Remote access
- Social networking websites
- Online shopping websites
- Specific applications
See Configuring the Content Filter and Application awareness in Kerio Control for details.
In the example scenario, users authenticate via RADIUS for web access and Kerio Control forbids peer-to-peer networking.
- The administrator enables Always require users to be authenticated…… and Enable WPA2 enterprise clients authentication in Domains and User Login > Authentication Options . For more information refer to Using RADIUS server in Kerio Control.
- In Content Filter, the administrator enables the default rule Peer-to-PeerA distributed application architecture that partitions tasks or workloads between peers. traffic.
Traffic Rules define the types of permitted or denied network communication. By default the firewall creates a basic policy that permits all outgoing types of traffic. Examples of Traffic Rules include:
- Allowing or denying a particular type of network service (e.g., SMTP).
- Opening ports for incoming connections (Port mapping). For more information refer to Configuring traffic rules.
- Forcing specific outbound traffic through an interface. For more information refer to Configuring policy routing.
In the example scenario, the firewall routes incoming traffic to servers located on the DMZ network. The administrator creates port mapping rules to allow incoming connections. See Configuring traffic rules - multihoming and Configuring Demilitarized Zone (DMZ) for details.
Enabling remote access
You can use Virtual Private Networking (VPN) to allow remote users or entire networks to access services inside the local network. Kerio Control implements IPsecInternet Protocol security - A network protocol used to encrypt and secure data sent over a network. for mobile device access and tunneling with third-party VPN gateways. You can also use the proprietary Kerio VPN implementation for remote access from desktop operating systems, and for tunneling to other Kerio Control firewalls. You can manage settings for VPN in the VPN server interface of the Interfaces dialog box.
See Configuring Kerio VPN tunnel, Configuring IPsec VPN , and Configuring SSL certificates in Kerio Control for details.
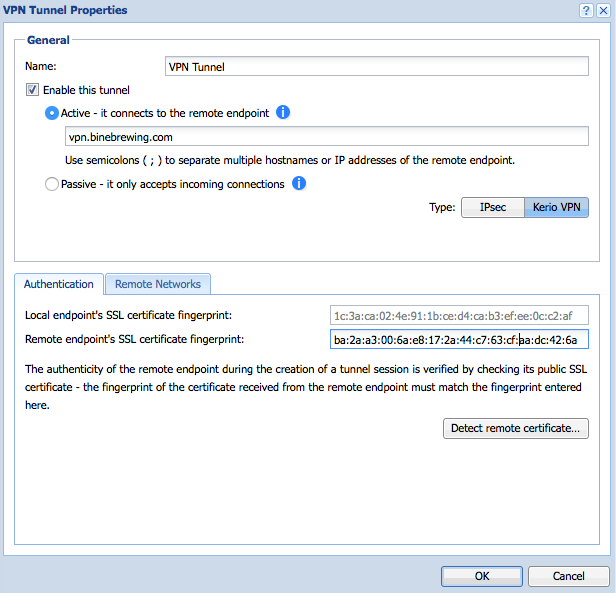
In the example scenario, Kerio Control maintains a VPN tunnel with a remote office, and users connect remotely using VPN from computers and mobile devices.
- The administrator enables the default traffic rule called VPN Services.
- The administrator modifies the user template to allow all users to connect using VPN.
- The administrator installs a signed SSL certificateSSL certificates are used to authenticate an identity on a server. and assigns it to the VPN serverKerio Control includes a VPN server which provides users to connect to the Kerio Control network from the Internet securely..
- The administrator creates a Kerio VPN tunnel to the branch office.
- The administrator assigns a preshared key to the IPsec VPN server.
- Users add IPsec / L2TP accounts on their mobile device.
- Users install and configure the Kerio VPN client on their desktop or laptop computers.
Managing bandwidth
Kerio Control includes several features to help you monitor network activity and optimize Internet availability.
| Section | Description |
|---|---|
| Active Hosts | Displays real-time activities of all hosts on the network. You can see which devices consume the most bandwidth, when the network is most active, and what types of activities are taking place. For more information refer to Monitoring active hosts. Status > Traffic Charts displays throughput totals for a variety of items, including network interfaces, traffic rules, or bandwidth rules. This information helps you identify how data flows through your network. |
| Traffic Charts | Displays throughput totals for a variety of items, including network interfaces, traffic rules, or bandwidth rules. This information helps you identify how data flows through your network. |
| Interfaces | Allows you to distribute network traffic between multiple Internet links. You can further adjust the routing of outgoing connections using Traffic Rules. For more information refer to Configuring policy routing. |
| Bandwidth Management and QoSQuality of service - Network's ability to obtain maximum bandwidth and manage other network performance elements like latency, error rate and uptime. | Allows you to prioritize traffic based on a variety conditions. For more information refer to Configuring bandwidth management. |
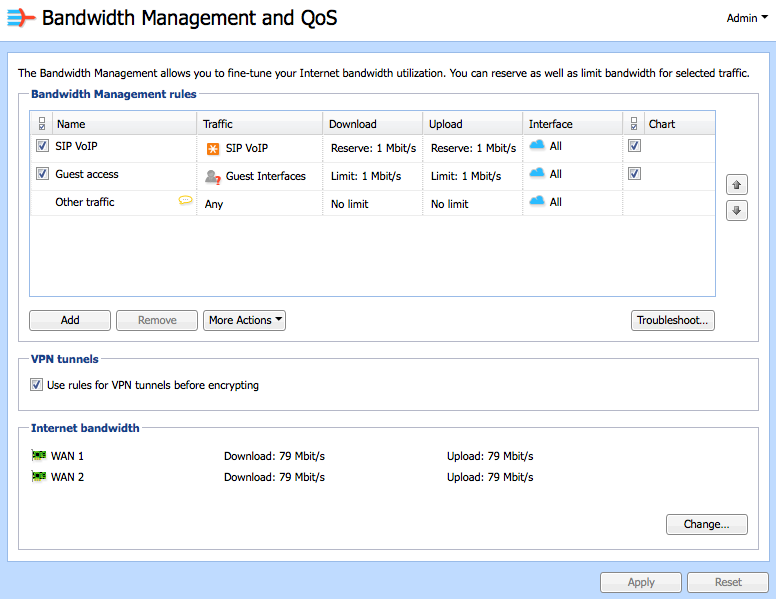
In the example scenario, Kerio Control reserves 1 Mbps for VoIP traffic and restricts guest access to a maximum of 1 Mbps.
- The administrator defines the Internet bandwidth for each Internet link.
- The administrator enabled default rule called SIPSession Initiation Protocol - Communication protocol used for voice and video calls in Internet telephony or private IP telephone systems. VoIP and sets the value to 1 Mbps.
- The administrator adds a new rule to limit Guest Interfaces to 1 Mbps.
Creating and viewing reports
Kerio Control includes a reporting feature called Kerio Control Statistics. Kerio Control Statistics records the activities of authenticated users to a local database on the firewall. Privileged users can access statistics information on demand through a special web interface, or by email. For more information refer to Configuring statistics and reports.
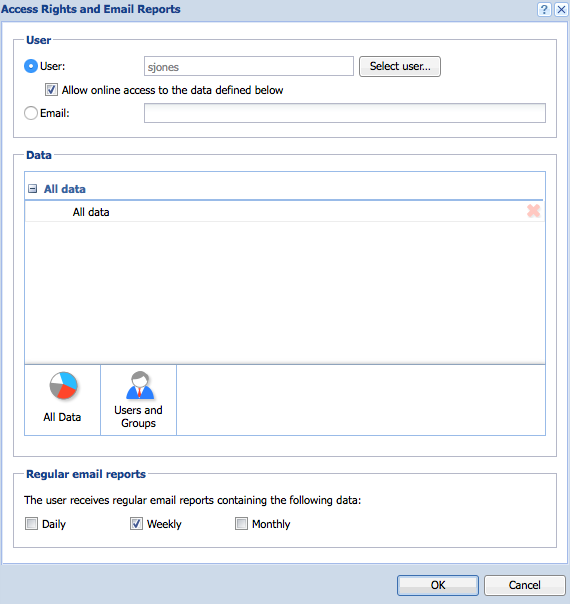
In the example scenario, the company president receives a weekly report of all user activity.
- The administrator defines an email address for the president’s user account.
- The administrator configures the firewall to gather Internet usage statistics.
- The administrator configures regular email reports for the company president.
Configuring automated backup
You can backup the Kerio Control configuration for restoring to another system in case of hardware failure or other types of disasters. You can backup the configuration manually from the Configuration Assistant, or automatically to MyKerio. In the example scenario, Kerio Control automatically saves its configuration to MyKerio every day. For more information refer to Saving configuration to MyKerio.