Configuring IPsec VPN tunnel
Kerio IPsecVPN tunnel allows the administrator to connect officers located on separated geographic areas into a single network.
Kerio IPsecInternet Protocol security - A network protocol used to encrypt and secure data sent over a network. VPN tunnelKerio Control includes a VPN tunnel which allows to distributed offices to interconnect their offices securely. offers authentication and encryption to ensure a fast and secure connection.
NOTE
To connect two or more Kerio Controls via VPNVirtual private network - A network that enables users connect securely to a private network over the Internet. tunnel, use Kerio VPN. Unlike Kerio IPsec VPN tunnel, Kerio VPN tunnel is able to seek routes in remote networks automatically.
To configure Kerio IPsec VPN tunnel:
Before you start
Prepare the following list:
- Enable the VPN Services pre-configured traffic rule on both tunnel endpoints.
- ID of the remote endpoint. In the most of servers it is called Local ID.
- A list of all routes behind the remote endpoint.
- If you want to use a SSL certificateSSL certificates are used to authenticate an identity on a server., prepare the SSLSecure Sockets Layer - A protocol that ensures integral and secure communication between networks. certificate of the remote endpoint, or an authority + ID of the remote SSL certificate. You must import the certificate or the authority to Kerio Control.
Configuring authentication method
You can select one of the following methods:
 Preshared key authentication
Preshared key authentication
This method is easier for set up. Both endpoints use the same password for authentication:
- In the administration interface, go to Interfaces.
- Click Add > VPN Tunnel.
- Type a name of the new tunnel.
- Set the tunnel as active and type the hostname of the remote endpoint. At least one endpoint must be set as active. The active endpoint establishes and maintains a connection to the passive endpoint.
- Select Type: IPsec.
- Select Preshared key and type the key.
- Copy the value of the Local ID field from Kerio Control to the Remote ID of the remote endpoint and vice versa. Predefined Local ID is the hostname of Kerio Control. If you change the Kerio Control hostname, Local ID is changed too.
- (Optionally) In the Phase 1 and 2 cipher, click Change and configure ciphers manually. It can be necessary if you want to connect Kerio Control with the third party firewall. For details, see Configuring IKE ciphers.
- On tabs Remote Networks and Local Networks, you must define all remote networks including subnet for VPN clients and all local networks which are not detected by Kerio Control.
- Save the settings.
 SSL certificate authentication
SSL certificate authentication
Authentication with a SSL certificate requires a valid SSL certificate on both endpoints.
- The SSL certificate of the remote endpoint is imported in the Kerio Control (Definitions > SSL Certificates).
- The authority that signed the remote certificate is imported in the Kerio Control (Definitions > SSL Certificates). You also need to know the Local ID (Distinguished name) of the remote certificate.
When the SSL certificate/Authority is imported, follow these instructions:
- In the administration interface, go to Interfaces.
- Click Add > VPN Tunnel.
- Type a name of the new tunnel.
- Set the tunnel as active and type the hostname of the remote endpoint. At least one endpoint must be set as active. The active endpoint establishes and maintains a connection to the passive endpoint.
- Select Type: IPsec.
- Select Remote certificate:
- Not in local store — only an authority was imported to Kerio Control. Copy the remote SSL certificate ID to the Remote ID field and vice versa: import the Kerio Control authority to the remote endpoint and copy the Local ID somewhere in the remote endpoint.
- Select the remote SSL certificate. Export the certificate from Kerio Control and import it to the remote endpoint.
- (Optionally) In the Phase 1 and 2 cipher, click Change and configure ciphers manually. It can be necessary if you want to connect Kerio Control with the third party firewall. For details, see Configuring IKE ciphers.
- Save the settings.
Configuring ciphers in key exchange (IKE)
NOTE
New in Kerio Control 9.2!
Kerio Control can use several IKE ciphers during the connecting and authorizing process of IPsec tunnel. In many cases, these ciphers are common between the endpoints and no custom configuration is necessary.
In other cases, you may need to assign custom ciphers. Therefore, you can configure IKE ciphers in Kerio Control manually:
 Configuring authentication
Configuring authentication
- In the administration interface, go to Interfaces.
- Select the IPsec VPN tunnel and click Edit.
- In the VPN Tunnel Properties dialog box, click Change on the Authentication tab.
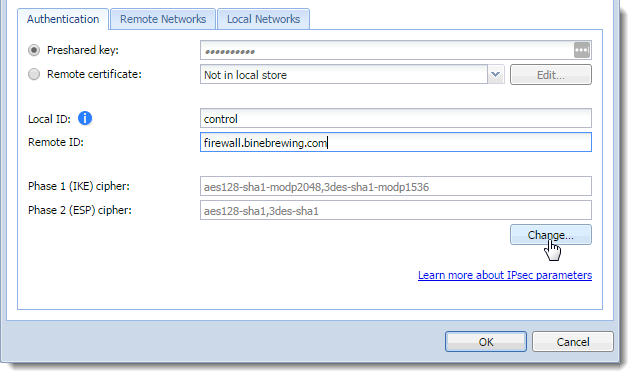
Configuring Authentication for the VPN tunnel
- In the VPN Tunnel Ciphers Configuration, select Custom ciphers.
- In drop down menus, change ciphers in the same way as they are set in the other firewall or device.
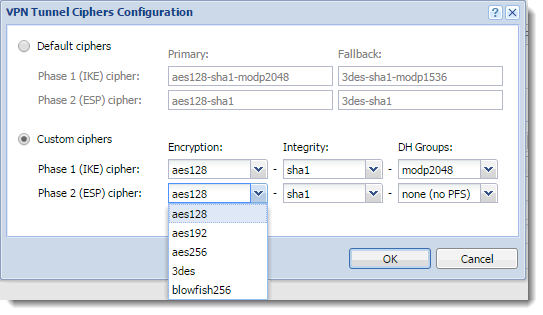
Configuring VPN Tunnel Ciphers
- Click OK twice.
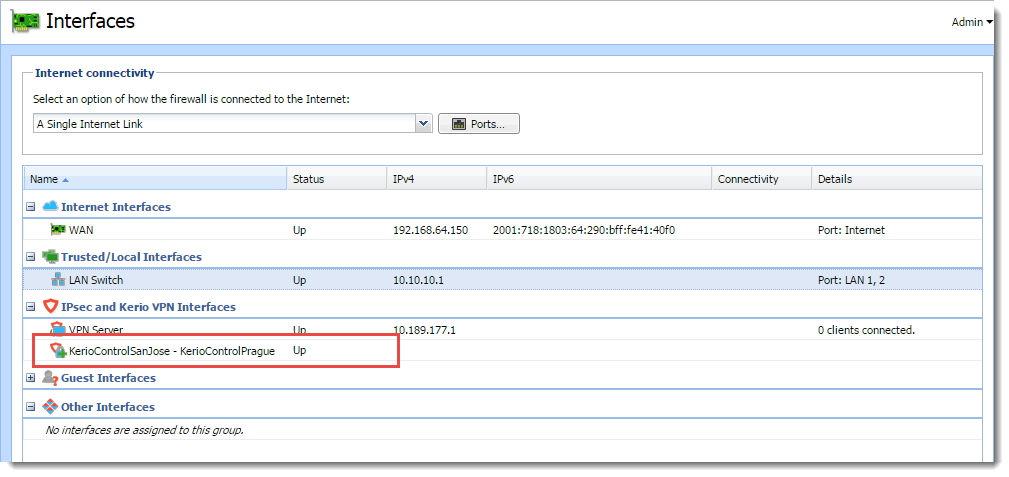
Interface node showing new VPN connection
Both endpoints should connect successfully and you can verify it in the Interfaces section. The IPsec tunnel is Up.
For more information refer to Default values in Kerio Control.
 Configuring local networks
Configuring local networks
Kerio Control IPsec tunnel can detect most of its local networks. To enable the automatic detection:
- In the administration interface, go to Interfaces.
- Select the IPsec VPN tunnel and click Edit.
- In the VPN Tunnel Properties dialog box, select Use automatically determined local networks. Automatically determined local networks are:
- All non-internet interfaces networks with no default route.
- Static networks.
- Remote networks of other IPsec tunnels.
- Manually specified custom remote networks of Kerio VPN tunnels.
- VPN subnet.
- If you define custom routes, select Use custom networks too.
NOTE
To setup Kerio VPN — IPsec VPN interoperability, also add networks connected via Kerio Control VPN which are not defined manually in the Kerio VPN tunnel configuration.
- Click OK.
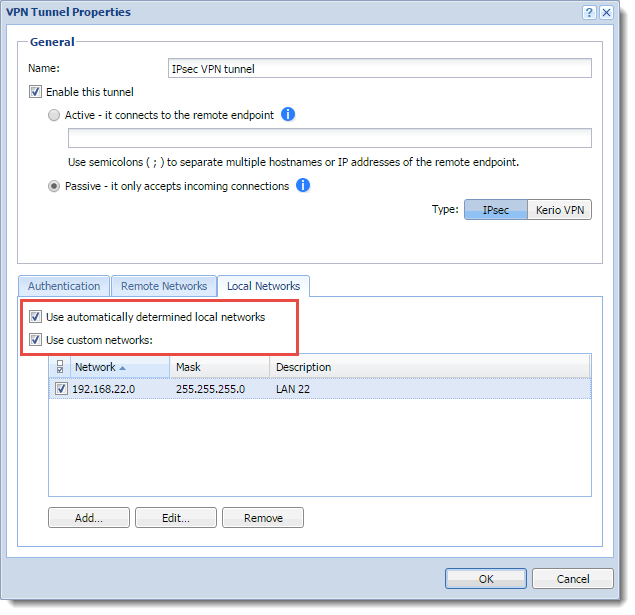
Configuring local networks
Networks from the following interfaces are not detected automatically:
- Interfaces from the Internet Interfaces group
- Interfaces with a default route
- Networks dynamically discovered by Kerio VPN
 Configuring remote networks
Configuring remote networks
IPsec VPN is not able to seek remote routes. You must enter them manually. For more information refer to Configuring the IPsec VPN tunnel.
Configuring VPN failover
If Kerio Control is load balancing between multiple Internet links, it is possible to use VPN failover. This ensures that a VPN tunnel is re-established automatically in case the primary link used for VPN tunneling becomes unavailable.
To configure failover:
- In the administration interface, go to Interfaces.
- Select the IPsec VPN tunnel and click Edit.
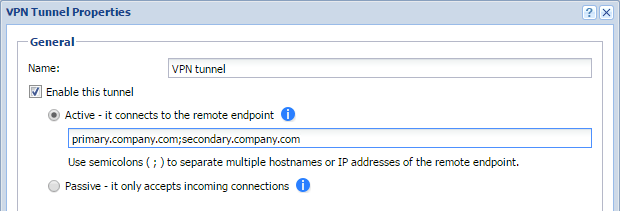
Configuring failover
- input all remote endpoints (by hostname or IP address), separated by semicolons, into the VPN tunnel properties.
NOTE
When attempting to establish the tunnel, Kerio Control cycles through the list of the endpoints in the same order that they are listed in the VPN Tunnel Properties.