Using the Connection log
Logs keep information records of selected events occurred in or detected by Kerio Control. For more information about configuring and using logs, see article Configuring and using logs in Kerio Control.
The Connection log gathers:
- traffic matching traffic rules with the Log connections enabled,
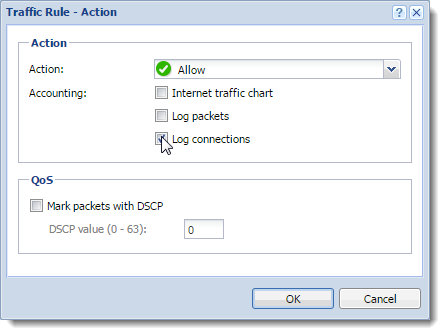
- log of UPnP traffic with the Log connections enabled (Security Settings > Zero-configuration Networking),
- information on IPv6Version 6 of the Internet Protocol. connections with the Log connections enabled (Security Settings > IPv6).
Reading the Connection log
[18/Apr/2013 10:22:47] [ID] 613181 [Rule] NATNetwork address translation - A method that remaps IP addresses by changing network address information.
[Service] HTTPHypertext Transfer Protocol - protocol for exchange of hypertext documents in HTML. [User] winston [Connection]
TCPTransmission Control Protocol - ensures packet transmission. 192.168.1.140:1193 > hit.google.com:80
[Duration] 121 sec [Bytes] 1575/1290/2865 [Packets] 5/9/14
[18/Apr/2013 10:22:47]— date and time when the event was logged (Note: Connection logs are saved immediately after a disconnection)[ID] 613181— Kerio Control connection identification number.[Rule] NAT— name of the traffic rule which has been used (arule by which the traffic was allowed or denied).[Service] HTTP— name of acorresponding application layer service (recognized by destination port). If the corresponding service is not defined in Kerio Control, the[Service]item is missing in the log.[User] winstonname of the user connected to the firewall from a host which participates in the traffic. If no user is currently connected from the corresponding host, the[User]item is missing in the log.[Connection] TCP 192.168.1.140:1193 - hit.top.com:80— protocol, source IP addressAn identifier assigned to devices connected to a TCP/IP network. and port, destination IP address and port. If an appropriate log is found in the DNSDomain Name System - A database enables the translation of hostnames to IP addresses and provides other domain related information. module cache, the host's DNS name is displayed instead of its IP address. If the log is not found in the cache, the name is not detected (such DNS requests would slow Kerio Control down).[Duration] 121 sec— duration of the connection (in seconds)[Bytes] 1575/1290/2865— number of bytes transferred during this connection (transmitted /accepted /total).[Packets] 5/9/14— number of packets transferred through this connection (transmitted/accepted/total).