Creating a new protection policy
GFI EndPointSecurity ships with a default protection policy so that the software is operational upon installation. You can create further protection policies to suit your company’s device access security policies.
To create a new protection policy:
- Click Configuration tab > Protection Policies.
- From Common tasks, click Create new protection policy….
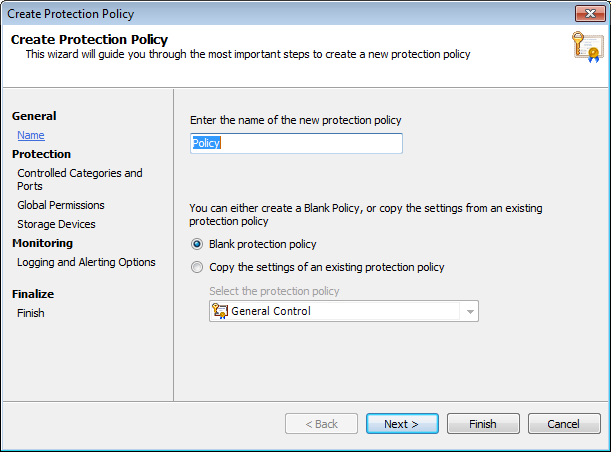
Creating a new policy - General settings
- Key in a unique name for the new protection policy.
- Select whether you want to create a blank policy or copy the settings from an existing policy. Click Next.In the settings area select the required settings inheritance option from:
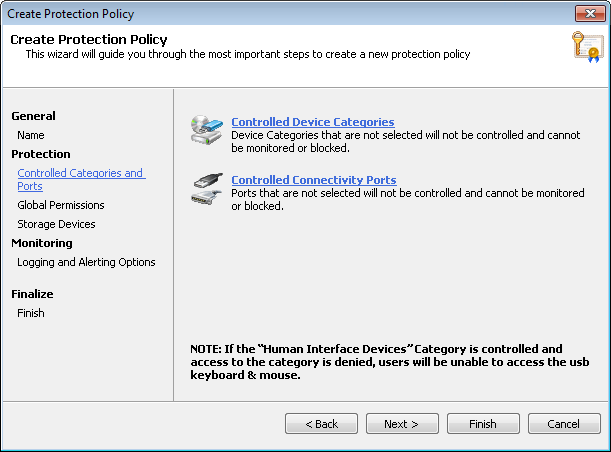
Creating a new policy - Controlled Categories and Ports settings
- Click Controlled Device Categories.
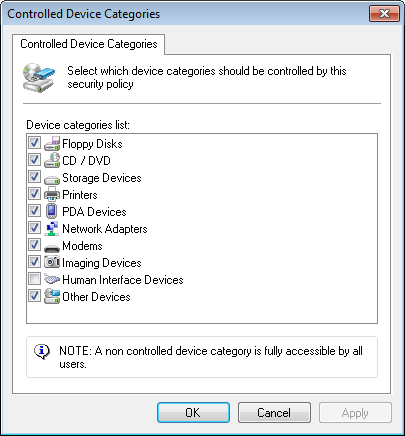
Controlled Device Categories options
- From the Controlled Device Categories dialog, select the required device categories you want to control by this new policy. Click OK to close the Controlled device categories dialog and return to the wizard.
Important
If Human Interface DevicesA specification that is part of the universal serial bus (USB) standard for a class of peripheral devices. These devices, such as a mice, keyboards, and joysticks, enable users to input data or to interact directly with the computer. is enabled and access is denied, users will not be able to use USB keyboards and mice connected to target computers protected by this policy.
- Click Controlled Connectivity Ports.
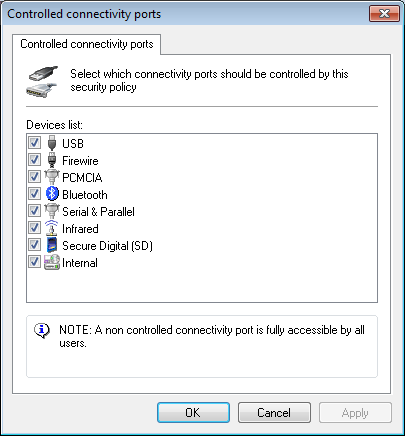
Controlled connectivity ports options
- From the Controlled connectivity ports dialog, select the required connectivity ports that you want to control by this new policy. Click OK to close the Controlled connectivity ports dialog and return to the wizard.
- Click Next.
Creating a new policy - Global Permissions settings
- Block any access to the controlled devices - to block access to all selected devices/ports.
- Allow everyone to access the controlled devices - to allow access to all selected devices/ports. If this option is selected, activity monitoring will still be carried out on target computers covered by the protection policy.
- Click Next.
- Click File-Type Filter and add the file-types to block/allow by this policy.
Note
GFI EndPointSecurity enables you to restrict access based on file-types. It is also able to identify the real content of most common file-types, (example: .DOC or .XLS files), and take the necessary actions applicable for the true file-type. This is most useful when file extensions are maliciously manipulated. For more information refer to Configuring file-type filters.
- Click OK to close the File-Type Filter dialog and return to the wizard.
- Click Encryption and enable/configure the preferred encryption engine.
Note
In addition, GFI EndPointSecurity can also allow or block Active DirectoryA technology that provides a variety of network services, including LDAP-like directory services. (AD) users and/or user groups, from accessing specific file-types stored on devices that are encrypted with BitLocker To GoA Microsoft Windows 7 feature to protect and encrypt data on removable devices.. These restrictions are applied when the encrypted devices are connected to the target computers covered by the protection policy. For more information refer to Configuring security encryption.
- Click OK to close the Encryption dialog and return to the wizard.
- Click Next.
- From Storage Devices, select the required options that you want to control from the tabs described below:
| Tab | Description |
|---|---|
| File-Type Filter |
GFI EndPointSecurity enables you to specify file-type restrictions on files, such as .DOC or .XLS files, being copied to/from allowed devices. You can apply these restrictions to Active Directory (AD) users and/or user groups. |
| Content Awareness |
GFI EndPointSecurity enables you to specify the file content restrictions for a particular protection policy. The content awareness feature looks into files transiting the endpoints via removable devices and it \identifies content based on pre-configured and custom regular expressions and dictionary files. By default the module looks for secure confidential details such as social security numbers and primary account numbers as well as information related to companies and enterprises such as names of diseases, drugs, dangerous chemicals and also trivial language or ethnic / racist terms.
|
| File Options | GFI EndPointSecurity enables you to specify the options required to block or allow files based on size. GFI EndPointSecurity also enables you to ignore large files when checking file type and content and archived files. |
| Encryption | GFI EndPointSecurity enables you to configure settings that specifically cater for encrypted devices. It also enables you to encrypt devices that are not yet secured. |
Note
For more information refer to For more information refer to Customizing Protection Policies.
- Configure logging and alerting options for this policy and click Next.
Note
For more information, refer to Configuring event logging and Configuring alerts.
- Review the summary page for information about your policy and click Finish.