Configuring security encryption
GFI EndPointSecurity enables you to configure settings which specifically cater for encrypted devices. It also enables you to encrypt devices which are not yet secured.
This section contains information about:
Configuring Microsoft BitLocker To Go devices
GFI EndPointSecurity can detect storage devices encrypted with Microsoft BitLocker To GoA Microsoft Windows 7 feature to protect and encrypt data on removable devices.. This enables you to configure different permissions on such devices.
NOTE
The permissions giving to the users under Enable detection of encrypted devices only takes effect if the storage device is encrypted with Microsoft BitLocker To Go encryption.
To enable Microsoft BitLocker To Go detection:
- From GFI EndPointSecurity management console, click Configuration tab > Protection Policies.
- From the left pane, select the protection policy for which to apply the encryption policy.
- From the right pane, click Encryption in the Security section.
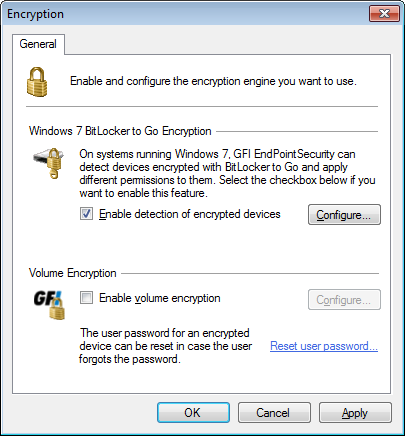
Encryption options - General tab
- Select Enable detection of encrypted devices and click Configure.
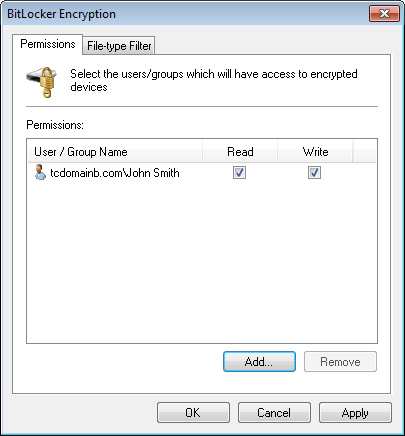
Encryption options - Permissions tab
- Click Add… to specify the users and groups with access to encrypted devices.
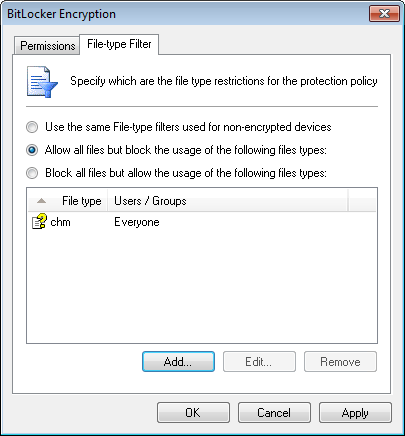
Encryption options - File-type Filter tab
- Select the File-type Filter tab to configure the file-types to restrict.
- Select the restriction to apply to this policy:
- Use the same File-type filtersA set of restrictions that are assigned to users and groups per file-type. Filtering is based on file extension checks and real file type signature checks. used for non-encrypted devices
- Allow all files but block the usage of the following file types
- Block all files but allow the usage of the following file types.
- Use the Add, Edit and Remove buttons, to manage file types.
- Click OK.
Configuring Volume Encryption
Volume Encryption enables you to encrypt the contents of USB devices using AES 256 encryption. When volume encryption is enforced, users must provide a password to encrypt or access storage devices data. To enforce Volume Encryption on installed agents:
Note
Encryption on demand is possible even if not forced by the administrator directly by the end user by clicking the Encrypt... entry from the shell context menu of a removable drive.
- From GFI EndPointSecurity management console, click Configuration tab > Protection Policies.
- From the left pane, select the protection policy for which to apply encryption policy.
- From the right pane, click Encryption in the Security section.

Encryption options - General tab
- Select Enable volume encryption. Click Configure. Click Reset user password to reset the encryption password for a specific user.
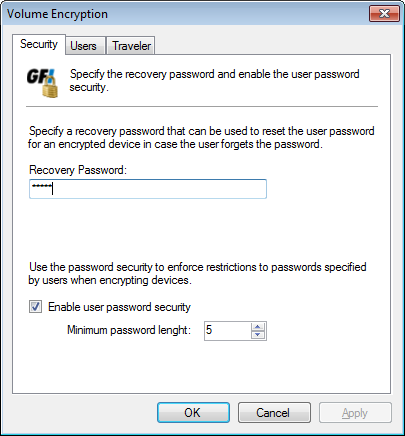
Encryption options -Security tab
- From the Security tab, configure the features described below:
| Option |
Description |
|---|---|
| Recovery Password |
Key in a password used if users forget or lose their passwords. |
| Enable user password security | Enforce restrictions to passwords specified by end users. In Minimum password length, specify the minimum acceptable password length. |
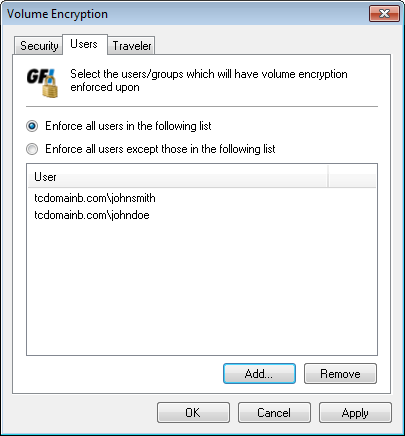
Encryption options - Users tab
- Select Users tab and configure the following options:
| Option |
Description |
|---|---|
| Enforce all users in the following list | Select the users that will have volume encryption enforced on their portable devices. Use the Add and Remove buttons to manage selected users. |
| Enforce all users except those in the following list | Select the users that will be exempt from volume encryption. Use the Add and Remove buttons to manage selected users. |
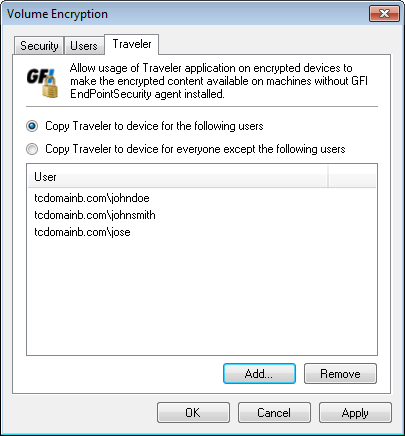
Encryption options - Traveler tab
Note
Traveler is an application that can be automatically installed on storage devices using GFI EndPointSecurity. This application enables you to un-encrypt data encrypted by GFI EndPointSecurity on storage devices, from computers that are not running a GFI EndPointSecurity Agent.
- Select Traveler tab and configure the following options:
| Option |
Description |
|---|---|
| Copy Traveler to device for the following users |
Select the users that will have Traveler installed on their machines. Use the Add and Remove buttons to manage selected users. |
| Copy Traveler to device for everyone except the following users | Select the users that will be exempt from having Traveler installed. Use the Add and Remove buttons to manage selected users. |
- Click Apply and OK.