Monitoring EndPoint Control
GFI OneGuard EndPoint ControlService used by GFI OneGuard to control access to devices. brings a dashboard that offers administrator an overview of devices usage and a table that shows the details of every device accessed showing the user, the application, the data and the status of blocked or allowed for every access.
The information is available in the format of reports that can be run at any time and schedule for recurrent patterns. For more information refer to Reports.
To monitor the status of the EndPoint Control service and track usage history of devices, go to DashboardA graphical representation that indicates the status of various operations that might be currently active, or that are scheduled. > EndPoint Control.
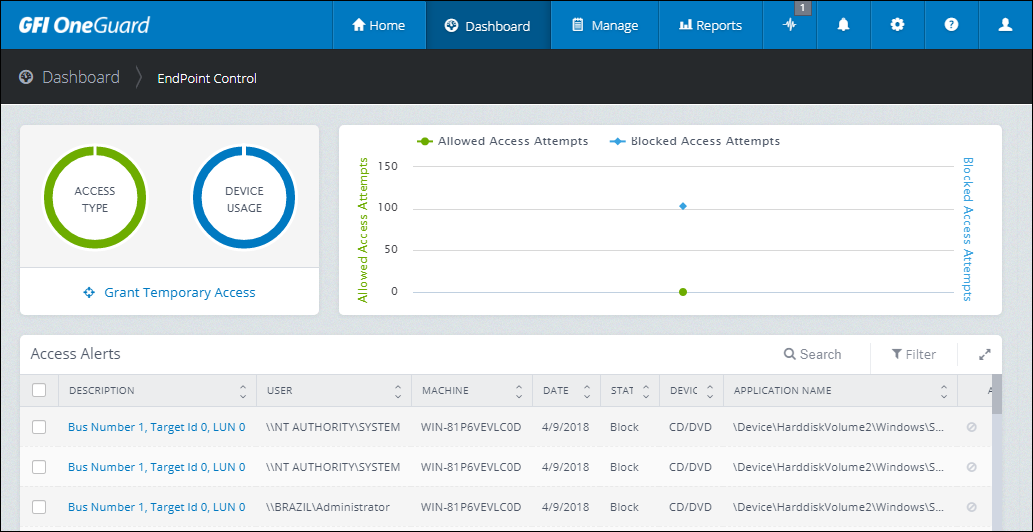
The EndPoint Control dashboard
The top widgets show a graphical representation of device usage over time, displaying allowed access attempts and blocked access attempts. The graph offers a good overview of trend user behavior regarding attempts to break policy rules.
The lower widget shows a table with the access alerts in chronological order. The widget displays the user, machine, category, time and application used when the device was allowed or blocked.
From this dashboard you can perform the following actions:
| Action | Description |
|---|---|
| Grant Temporary AccessFeature that allows temporary access to devices blocked by an EndPoint Control policy. |
EndPoint Control enables administrators to grant temporary access to users. The Temporary Access feature allows time-limited access to peripherals like a USB or CD/DVD blocked by an EndPoint Control policy. This feature can be used to give flexibility and manage exceptions without compromising security. For example, when a guest room that provides limited access to external clients needs to be used to hold a short conference. For more information refer to Temporary Access. |
| Search | Key in the terms to search for in the Access Alerts table. Any fields matching the term are returned in real time. |
| Filter |
Narrow down you search the following criteria:
|
| Delete alerts | Click the icon in the action column to delete the alert from the table. |