How GFI EndPointSecurity works - Temporary Access
GFI EndPointSecurity temporary access operations can be divided in three logical stages:
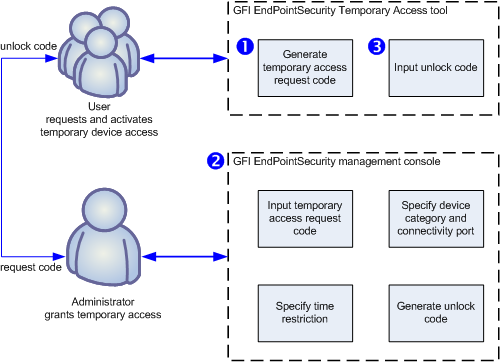
Requesting/granting temporary access
The table below describes the stages depicted above:
| Stage | Description |
|---|---|
| Stage 1 - User requests temporary device access | The user executes the GFI EndPointSecurity Temporary Access tool from the computer on which the device is to be accessed. The tool is used to generate a request code, which the user communicates with the administrator. The user also needs to inform the administrator on the device types or connection ports that need to be accessed, and for how long will devices/ports access be required. |
| Stage 2 - Administrator grants temporary access | The administrator uses the Temporary Access feature within the GFI EndPointSecurity management console to enter the request code, specify devices/ports and time restrictions. An unlock code is generated which the administrator then communicates with the user. |
| Stage 3 - User activates temporary device access | Once the user receives the unlock code sent by the administrator, this code is entered in the GFI EndPointSecurity Temporary Access tool to activate the temporary access and to be able to use the required devices/ports. |