How GFI EndPointSecurity works - Device Access
GFI EndPointSecurity device access operations can be divided in three logical stages:
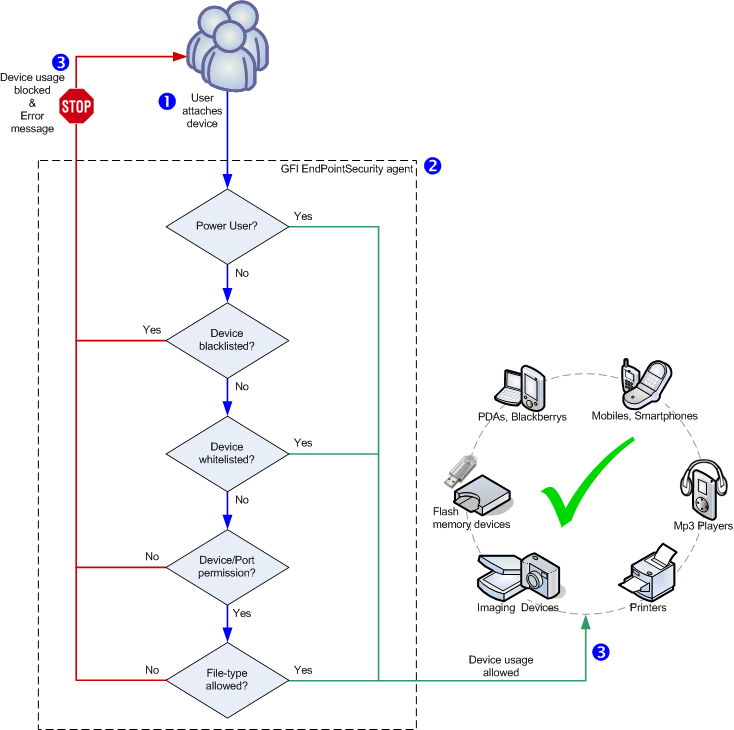
Device access
The table below describes the stages depicted above:
| Stage | Description |
|---|---|
| Stage 1 - Device attached to computer | The user attaches a device to a target computer protected by GFI EndPointSecurity. |
| Stage 2 - Protection policyA set of device access and connectivity port permissions that can be configured to suit your company’s device access security policies. enforcement | The GFI EndPointSecurity agent installed on the target computer detects the attached device and goes through the protection policy rules applicable to the computer/user. This operation determines whether the device is allowed or blocked from being accessed. |
| Stage 3 - Device usage allowed/blocked | The user either receives an error message indicating that device usage has been blocked, or else is allowed to access the device. |