Configuring event logging
GFI EndPointSecurity agents record events related to attempts made to access devices and connection ports on target computers. The agents also record events related to service operations. You can specify where these events are to be stored, and also what types of events are to be logged. You can do this on a policy by policy basis.
To specify logging options for users in a protection policy:
- Click Configuration tab > Protection Policies.
- From Protection Policies > Security, select the protection policy to configure.
- From the right pane, click Set Logging Options in the Logging and Alerting section.
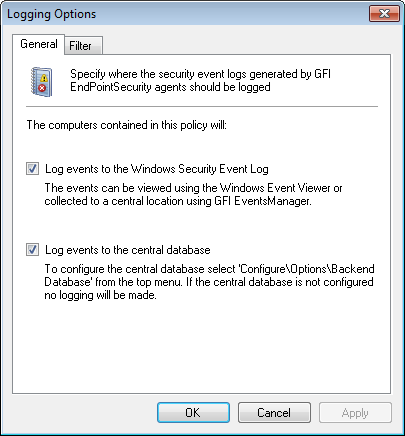
Logging Options - General tab
- In the Logging Options dialog, click General tab.
- Enable or disable the locations where to store events generated by this protection policy:
| Option |
Description |
|---|---|
| Log events to the Windows Security Event Log | you can view events through the Windows Event Viewer of every target computer or through GFI EventsManager after they are collected in a central location |
| Log events to the central database | you can view the events within the Logs Browser sub-tab in the GFI EndPointSecurity management console. This option requires the configuration of a central database. For more information refer to Managing the Database Backend. |
If both options are enabled, then the same data is logged in both locations.
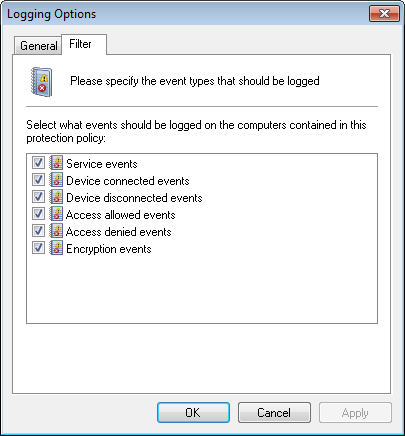
Logging Options - Filter tab
- Select Filter tab, and select any of the following event types to log by this protection policy. Click OK.
To deploy protection policy updates on target computers specified in the policy:
- Click Configuration tab > Computers.
- From Common tasks, click Deploy to all computers….